2024.4.26, San Gabriel Valley Woman Pleads Guilty to Counterfeit Postage Fraud that Caused More Than $150 Million in Losses to U.S. Postal Service
San Gabriel Valley Woman Pleads Guilty to Counterfeit Postage Fraud that Caused More Than $150 Million in Losses to U.S. Postal Service
Friday, April 26, 2024
For Immediate Release
U.S. Attorney’s Office, Central District of California
LOS ANGELES – A San Gabriel Valley woman pleaded guilty today to defrauding the United States Postal Service (USPS) out of more than $150 million by using counterfeit postage to ship tens of millions of parcels.
Lijuan “Angela” Chen, 51, of Walnut, pleaded guilty to one count of conspiracy to defraud the United States and one count of use of counterfeit postage. Chen has been in federal custody since her arrest in May 2023.
“This defendant participated in a fraud scheme that caused massive losses to our nation’s postal service,” said United States Attorney Martin Estrada. “My office will continue to focus on holding fraudsters accountable and bringing justice to victims everywhere.”
According to her plea agreement, from at least November 2019 to May 2023, Chen and her co-defendant, Chuanhua “Hugh” Hu, 51, owned and operated a package shipping business located in the City of Industry. This company provided shipping services, including the shipping of packages via U.S. Mail, for China-based logistics businesses.
To avoid the cost of postage, Hu began creating false and counterfeit postage to ship packages by printing duplicate and counterfeit Netstamps – stamps that may be purchased online from third-party vendors and printed onto adhesive paper.
In November 2019, knowing that law enforcement was investigating his use of counterfeit postage, Hu fled the United States and moved to China. After fleeing to China, Hu developed ways to make counterfeit postage and avoid detection, such as a computer program for fabricating counterfeit postage shipping labels. Chen remained in the United States and managed the warehouses that she and Hu used to ship mail bearing counterfeit postage.
Starting in 2020, Chen and Hu began affixing counterfeit postage to mail they presented to USPS for delivery. Chen and Hu received parcels from the China-based vendors and others, applied shipping labels showing postage purportedly paid and then arranged for the parcels to be transferred to USPS facilities to be shipped across the nation. The shipping labels were fraudulent and frequently included, among other red flags, “intelligent barcode data” recycled from previously mailed packages, according to court documents. Intelligent barcode data is used in some postage shipping labels to evidence the payment of required postage for the shipped item.
For example, on October 25, 2022, Chen and Hu caused to be transported to USPS a delivery of approximately 4,779 packages to be shipped via U.S. Mail. This delivery included multiple packages bearing counterfeit USPS Priority Mail postage meter stamps.
From January 2020 to May 2023, Chen and Hu knowingly mailed and caused to be mailed more than 34 million parcels containing counterfeit postage shipping labels, which caused more than $150 million in losses to USPS.
As part of her plea agreement, Chen has agreed to forfeit funds that law enforcement seized from her bank accounts, insurance policies, and real estate in Walnut, Chino, Chino Hills, South El Monte, Diamond Bar, and West Covina.
“The Postal Service and the Postal Inspection Service will continue to implement expanded measures to preserve the level of security Postal Service customers expect and deserve,” said Inspector in Charge Carroll Harris, Los Angeles Division of the Postal Inspection Service. “Engaging in counterfeit postage fraud causes monetary losses to customers and the Postal Service alike. Fraudsters beware, the Postal Inspection Service will continue to exhaust all its efforts to disrupt your scheme, find you, and bring you to justice.”
“Ms. Chen has admitted today that she conspired with Mr. Hu to defraud the United States Government willfully and knowingly,” said Special Agent in Charge Tyler Hatcher, IRS Criminal Investigation, Los Angeles Field Office. “IRS:CI will work tirelessly with our partners to protect taxpayer interests in the postal service and other government agencies.”
United States District Judge Josephine L. Staton scheduled an August 2 sentencing hearing, at which time Chen will face a statutory maximum sentence of five years in federal prison for each count.
Hu, who is believed to be a fugitive residing in China, is charged with one count of conspiracy to defraud the United States, three counts of passing and possessing counterfeit obligations of the United States, and one count of forging and counterfeiting postage stamps.
An indictment is merely an allegation, and the defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt in a court of law.
The United States Postal Inspection Service and IRS Criminal Investigation investigated this matter.
Assistant United States Attorneys James C. Hughes and Richard E. Robinson of the Major Frauds Section are prosecuting this case.
—
Southern California woman pleads guilty in $150-million counterfeit postage scheme
A San Gabriel Valley woman who was accused of using counterfeit postage on tens of millions of packages pleaded guilty Friday to defrauding the United States Postal Service out of more than $150 million.
Lijuan “Angela” Chen, 51, pleaded guilty to one count of conspiracy to defraud the U.S. and one count of using counterfeit postage, according to a statement from the U.S. Justice Department.
Chen, a resident of Walnut, has been in federal custody since she was arrested in May 2023. A co-defendant, 51-year-old Chuanhua “Hugh” Hu — who authorities say is considered a fugitive hiding in China — has been charged with one count of conspiracy to defraud the U.S., three counts of passing and possessing counterfeit obligations of the U.S. and one count of forging and counterfeiting postage stamps.
In all, authorities allege that the duo mailed more than 34 million parcels containing counterfeit postage labels from January 2020 through last May.
According to Chen’s plea agreement, she and Hu owned and operated a City of Industry-based package shipping company that offered shipping by U.S. Mail for China-based logistics businesses.
Hu then began to print duplicate and counterfeit NetStamps in an effort to cut the cost of postage, authorities allege.
In November 2019, officials say, Hu became aware that federal authorities were investigating, so he fled to China, where he continued to create counterfeit postage and avoid detection. Federal authorities believe he used a computer program to fabricate shipping labels.
Meanwhile, Chen remained in the San Gabriel Valley, managing the warehouses the two used to ship packages for their business. The pair then began using counterfeit postage to ship items by U.S. Mail in 2020. Authorities say they would receive packages from China-based companies and apply the fake postage to ship them through the Postal Service.
According to court documents, the red flags raised by fake postage included the reuse of “intelligent barcode data” already applied to other mailed packages. Those data are used to prove the labels have been paid for prior to shipping.
Multiple packages shipped by Chen and Hu included counterfeit Priority Mail postage, authorities said.
Under the terms of Chen’s plea agreement, she will forfeit funds in her bank accounts, insurance policies and real estate in Chino, Chino Hills, Diamond Bar, South El Monte, Walnut and West Covina. She is scheduled to be sentenced in August, and faces up to five years in prison for each count.
“This defendant participated in a fraud scheme that caused massive losses to our nation’s postal service,” U.S. Atty. Martin Estrada said in a statement. “My office will continue to focus on holding fraudsters accountable and bringing justice to victims everywhere.”
—
洛華女詐騙超1.5億 多處房產被沒收 丈夫潛逃中國
洛杉磯縣聖蓋博谷(San Gabriel Valley)一名華人女子,日前承認偽造郵資(counterfeit postage)詐騙罪,對美國郵政局(USPS)造成超過1.5億元。她的同犯、也是她的丈夫,已潛逃回中國;夫妻倆在南加華人區擁有多處房產,均已被沒收。
根據加州中區檢察官辦公室(U.S. Attorney’s Office Central District of California)訊息,51歲的陳麗娟(Lijuan “Angela”Chen,音譯)4月26日認罪,承認使用假郵資運送數千萬個包裹,詐騙郵局超過1.5億的巨額資金。陳麗娟來自核桃市(Walnut),自2023年5月被捕以來,她一直被聯邦拘留。
作為認罪協議的一部分,陳麗娟同意執法部門沒收她的銀行帳戶、保險單以及多處房產;這些房產分別位於核桃市、奇諾市(Chino)、奇諾岡(Chino Hills)、南艾爾蒙地市(South El Monte)、鑽石吧(Diamond Bar)、以及西柯汶那市(West Covina)等城市。
根據陳麗娟的認罪內容,51歲的丈夫胡傳華(Chuanhua “Hugh” Hu)是同犯, 2019年11月至2023年5月期間,兩人在工業城(City of Industry)擁有並經營一家包裹運輸公司,該公司為中國物流企業提供運輸服務,包括透過美國郵政運送包裹。為逃避郵資成本,胡傳華透過偽造的Netstamps郵票,製造虛假郵資運送包裹;Netstamps是一種可以從第三方供應商在線購買,並印在不干膠紙上的郵票。
2019年11月,胡傳華得知執法部門正在調查他的違法行為,隨即逃往中國,並在中國繼續研究製作假郵資並逃避檢測的方法。例如使用電腦程式偽造運輸標籤。期間,妻子陳麗娟則留在洛杉磯,管理兩人用來運送假郵資郵件的倉庫。
從2020年開始,夫妻倆開始在USPS投遞的郵件上貼假郵資。他們從一些中國供應商接收包裹後,貼上顯示已付郵資的運輸標籤,然後將這些包裹轉移到美國郵政局,以便運往全國各地。法庭文件顯示,這些運輸標籤充滿欺詐性,包含從先前郵寄的包裹中回收的「智慧條形碼」;一些郵資運輸標籤中使用智慧條形碼,證明已支付運輸物品所需的費用。
例如,2022年10月25日,陳麗娟、胡傳華兩名嫌犯將4779個包裹透過郵局運送,大多包裹均貼有偽造的USPS Priority Mail郵資計價郵票。2020年1月至2023年5月,兩人共郵寄超過3400萬個含有假郵資運輸標籤的包裹,給郵政局造成超過價值1.5億元的損失。
嫌犯在USPS投遞的郵件上貼假郵資,運往全美各地。圖為示意圖。
華人夫妻偽造郵資,對USPS造成超過1.5億元的損失。圖為示意圖。
據悉,陳麗娟量刑聽證會將於8月2日舉行,每項罪名將面臨長達5年監禁。同案犯胡傳華仍在逃中國,他被控串謀詐騙聯邦機構、傳播和持有偽造托運義務(counterfeit obligations)、以及偽造郵票罪。美國郵政局和國稅局刑事調查局正對此案進行調查。檢察官Martin Estrada指出,被告參與詐騙計畫,對國家郵政服務造成巨大損失,執法部門將繼續致力追究欺詐者責任,為受害者伸張正義。
2024.4.18, Suspect arrested for defrauding the elderly
The suspect was identified as Huiming Yu, a 27-year-old male from the city of Alhambra. He was subsequently arrested for PC 532(a) – Theft by False Pretenses and booked at the West Valley Detention Center.
Ontario Police Department, California
Thursday April 18th, 2024 :: 05:14 p.m. PDT
Suspect arrested for defrauding the elderly
Ontario, CA – The ORION Taskforce has arrested a suspect for defrauding the elderly and returned approximately $500,000 to identified fraud victims.
The Ontario Regional Interdiction of Narcotics (ORION) Taskforce is made up of officers from the Ontario and Upland Police departments. Together, they work to combat financial fraud and illegal narcotics being shipped across the country.
In late January of 2024, ORION Taskforce Officers intercepted fraud-related packages shipped from all over the country to several Southern California drug stores. Through their investigation, Taskforce Officers learned the receivers’ names on the packages were false and that the elaborate scheme also involved financially defrauding elderly victims, by having the victims ship money to the suspect after false promises were made. These false promises included telling victims their computer was hacked or they needed protection from the FBI and to resolve these issues, they needed to ship money to the suspect.
The suspect was identified as Huiming Yu, a 27-year-old male from the city of Alhambra. He was subsequently arrested for PC 532(a) – Theft by False Pretenses and booked at the West Valley Detention Center.
There are believed to be over 30 victims and because of the Taskforce’s work, approximately $500,000 has been returned to the victims thus far.
We want to remind our communities to stay vigilant. Protect yourself from fraud by verifying identities by doing research, avoid unsolicited offers, and to seek advice if unsure. Report all suspicious activity to the police immediately.
Anyone with information is asked to contact the Ontario Police Department at (909) 986-6711 or Officer Jose Valencia at (909) 408-1606. Information can be reported anonymously by calling WE-TIP at 800-78-CRIME or online at www.wetip.com.
Address/Location
Ontario Police Department, California
2500 S Archibald Ave
Ontario, CA 91761
Contact
Emergency: 9-1-1
Non-emergencies: 909-395-2001
—
Southern California man busted for scamming elderly victims out of $500K
Posted: Apr 18, 2024
A 27-year-old man from the San Gabriel Valley has been arrested after allegedly defrauding elderly victims of more than $500,000, authorities announced Thursday.
The investigation into Alhambra resident Huiming Yu began in late January when detectives with the Ontario Police Department’s Regional Interdiction of Narcotics Task Force intercepted fraud-related packages sent from across the country to several Southern California drug stores, according to a department news release.
Investigators learned that the receivers’ names on the packages were false and that the elaborate scheme targeting elderly victims involved telling them their computer had been hacked and that they needed protection from the Federal Bureau of Investigation, for a fee, to resolve these matters.
The victims would then ship money to Yu based on the false promises he made.
Yu was arrested and booked at the West Valley Detention Center on charges of theft by false pretense.
Authorities believe there were more than 30 victims of the scam and have, so far, been able to return some $500,000 in stolen funds to those who were defrauded.
“We want to remind our communities to stay vigilant,” the release stated. “Protect yourself from fraud by verifying identities, doing research, avoiding unsolicited offers and seeking advice if unsure. Report all suspicious activity to the police immediately.”
Anyone with information about this investigation is asked to contact the Ontario Police Department at 909-986-6711 or Officer Jose Valencia at 909-408-1606.
Those wishing to remain anonymous can call the WeTip Hotline at 800-78-CRIME or leave tips online at WeTip.
—
詐騙長者逾三十人 南加華裔男子被捕
2024-04-20
當局本週宣布,一名來自聖蓋博谷的27歲華裔男子因涉嫌詐騙老年受害者超過50萬元而被逮捕。
KTLA 5電視新聞報道,安大略市警局指出,針對阿罕布拉市居民余慧明(Huiming Yu音譯)的調查始於1月下旬。
當時,地區緝毒工作小組的警探截獲了從全國各地發送到南加州幾間藥店的詐欺包裹。
調查人員了解到,包裹上的收件人姓名是虛假的,嫌犯專以老年人為下手目標,謊稱他們的電腦遭到駭客入侵,需要聯邦調查局付費保護才能解決問題。
余因涉嫌詐欺罪名被逮捕,並被關押在西谷看守所。
警方相信該場騙局至少有超過30名受害者,截至目前為止,警方已向受騙者返還約50萬的被騙現金。
新聞稿稱:「希望社區居民能保持警惕,透過驗證身分、深入了解、拒絕可疑報價以及尋求專業建議等措施保護自身免受詐欺,同時立即向警方通報所有可疑活動。」
知情者或受害者請聯繫安大略市警局:(909)986-6711或警官Jose Valencia:(909)408-1606。希望保持匿名者則可撥打WeTip熱線:800-78-CRIME或在www.wetip.com線上留言。
—
30位老人上当,受骗金额超$50万!洛杉矶华裔因诈骗被捕!
近日,一名来自洛杉矶华人区圣盖博谷(San Gabriel Valley)的27岁男子因涉嫌诈骗老年人50多万美元而被捕。
安大略警局称,对阿罕布拉居民 Huiming Yu 的调查始于1月下旬。当时,该警察局区域禁毒特遣部队(Regional prohibition of Narcotics Task Force)的侦探截获了从全美各地寄往南加州几家药店的与欺诈有关的包裹。
调查人员了解到,包裹上收款人的名字是假的,背后是一场针对老年人的经济诈骗。嫌犯告诉这些受害者,他们的电脑遭到了黑客攻击,他们需要联邦调查局的保护,并收取费用来解决这些问题。
然后,受害者会根据 Yu 的虚假承诺,把钱寄给他。
目前,Yu 已被逮捕,罪名是欺诈。
有关部门认为,这一骗局的受害人超过30个,到目前为止,已经能够将大约50万美元的被盗资金归还给受害人。
警方表示:“我们想提醒我们的社区保持警惕。通过验证身份、进行调查、避开主动提供的服务,以及在不确定的情况下寻求建议来保护自己免受欺诈。立即向警方报告所有可疑活动。”
2024.4.18, A Manhattan jury has found crypto trader Avi Eisenberg guilty of fraud and market manipulation for his $110 million heist from decentralized finance protocol Mango Markets in October 2022. Eisenberg was arrested in Puerto Rico in December 2022 and charged with commodities fraud, commodities manipulation, and wire fraud for the scheme. He will be sentenced on July 29 by New York District Court Judge Arun Subramanian. Eisenberg faces up to 20 years in federal prison for his crimes.
PRESS RELEASE
Man Convicted for $110M Cryptocurrency Scheme
Thursday, April 18, 2024
For Immediate Release
Office of Public Affairs
Justice Department’s First Cryptocurrency Open-Market Manipulation Case
A federal jury in New York convicted a man residing in Puerto Rico today of commodities fraud, commodities market manipulation, and wire fraud in connection with the manipulation on the Mango Markets decentralized cryptocurrency exchange.
According to court documents and evidence presented at trial, Avraham Eisenberg, 28, engaged in a scheme to fraudulently obtain approximately $110 million worth of cryptocurrency from Mango Markets and its customers by artificially manipulating the price of certain perpetual futures contracts.
“Avraham Eisenberg executed a manipulative trading scheme on a cryptocurrency exchange, defrauding the exchange and its investors out of $110 million,” said Principal Deputy Assistant Attorney General Nicole M. Argentieri, head of the Justice Department’s Criminal Division. “Manipulative trading puts our financial markets and investors at risk. This prosecution—the first involving the manipulation of cryptocurrency through open-market trades—demonstrates the Criminal Division’s commitment to protecting U.S. financial markets and holding wrongdoers accountable, no matter what mechanism they use to commit manipulation and fraud.”
“Moments ago, Avraham Eisenberg was found guilty by a unanimous jury in the first-ever cryptocurrency open-market manipulation case,” said U.S. Attorney Damian Williams for the Southern District of New York. “This ground-breaking prosecution epitomizes this office’s ability to employ innovative methods and cutting-edge law enforcement tools to continue to protect all financial markets. The career prosecutors of this office continue their expertise in prosecuting financial fraud, one of our core priorities, and would-be financial criminals should think twice before daring to engage in illicit conduct on our watch.”
“The FBI and its partners will not stand by when criminals engage in illicit activity at the expense of the American people and our financial institutions,” said Executive Assistant Director Timothy Langan of the FBI’s Criminal, Cyber, Response, and Services Branch. “If you engage in fraudulent activity, whether that be in the cryptocurrency space or through other forms of market manipulation, you will be held accountable for your ill-gotten gains.”
Eisenberg is scheduled to be sentenced on July 29 and faces a maximum penalty of 10 years in prison on the commodities fraud count and the commodities manipulation count, and a maximum penalty of 20 years in prison on the wire fraud count. A federal district court judge will determine any sentence after considering the U.S. Sentencing Guidelines and other statutory factors.
The FBI investigated the case, with assistance from Homeland Security Investigations and IRS Criminal Investigation.
Trial Attorney and Special Assistant U.S. Attorney Tian Huang of the Criminal Division’s Fraud Section, a member of the National Cryptocurrency Enforcement Team (NCET), and Assistant U.S. Attorneys Thomas Burnett and Peter Davis for the Southern District of New York are prosecuting the case.
The NCET was established to combat the growing illicit use of cryptocurrencies and digital assets. Within the Criminal Division’s Computer Crime and Intellectual Property Section, the NCET conducts and supports investigations into individuals and entities that are enabling the use of digital assets to commit and facilitate a variety of crimes, with a particular focus on virtual currency exchanges, mixing and tumbling services, and infrastructure providers. The NCET also works to set strategic priorities regarding digital asset technologies, identify areas for increased investigative and prosecutorial focus, and lead the department’s efforts to collaborate with domestic and foreign government agencies as well as the private sector to aggressively investigate and prosecute crimes involving cryptocurrency and digital assets.
—
Mango Markets Exploiter Avi Eisenberg Found Guilty of Fraud and Manipulation
Eisenberg faces up to 20 years in prison for his $110 million heist.
NEW YORK – A Manhattan jury has found crypto trader Avi Eisenberg guilty of fraud and market manipulation for his $110 million heist from decentralized finance protocol Mango Markets in October 2022.
Eisenberg was arrested in Puerto Rico in December 2022 and charged with commodities fraud, commodities manipulation, and wire fraud for the scheme. He will be sentenced on July 29 by New York District Court Judge Arun Subramanian. Eisenberg faces up to 20 years in federal prison for his crimes.
“This ground-breaking prosecution epitomizes this office’s ability to employ innovative methods and cutting-edge law enforcement tools to continue to protect all financial markets,” said Damian Williams, U.S. Attorney for the Southern District of New York, in a Thursday press statement. “The career prosecutors of this office continue their expertise in prosecuting financial fraud, one of our core priorities, and would-be financial criminals should think twice before daring to engage in illicit conduct on our watch.”
During his trial in New York’s Southern District, Eisenberg’s defense attempted to frame his trades on Mango Markets as “successful and legal,” arguing that they “fully complied” with the decentralized protocol’s scanty rules at the time of the heist.
But the 12-person jury didn’t buy it, instead siding with prosecutors’ arguments that Eisenberg’s actions constituted “brazen” fraud and manipulation.
Eisenberg is the latest crypto figure to be convicted of fraud, following shortly on the heels of FTX founder Sam Bankman-Fried’s conviction and subsequent 25 year sentence for his role in the collapse of FTX, and Terraform Labs co-founder Do Kwon being found liable for fraud in civil fraud case against him earlier this month.
On October 11, 2022, Eisenberg made three massive MNGO perpetual futures trades between himself, pumping the price over 1000% and then using his newly-created collateral to trick the protocol into allowing him to “borrow” $110 million in various cryptocurrencies.
But Eisenberg wasn’t “borrowing,” he was stealing – hours after the exploit, he posted an anonymous proposal to the Mango Markets decentralized autonomous organization (DAO) offering to return $67 million of his ill-gotten gains in exchange for a promise not to pursue charges against him and permission to pocket the rest.
Though Eisenberg’s defense team, headed by well-known crypto defense lawyer Brian Klein, argued that Eisenberg was acting within the law, prosecutors showed the jury a bucket of evidence – including internet searches for things like “statute of limitations market manipulation” and “FBI surveillance” and “elements of fraud” and his flight to Israel after his identity as the exploiter was unmasked – suggesting he knew his actions were criminal.
“We’re obviously disappointed, but we will keep fighting for our client,” Klein told CoinDesk. “We plan to file a number of post-trial motions.”
—
美法院判定 Mango 协议漏洞利用者 Avraham Eisenberg 犯下诈欺罪
2024/04/19
美法院判定 Mango 协议漏洞利用者 Avraham Eisenberg 犯下诈欺罪
根据彭博社报导,在美国首件涉及加密货幣操纵相关刑事指控的审判中,被控利用 Solana 生態去中心化金融平台 Mango Markets 的漏洞窃取 1.1 亿美元的交易员 Avraham Eisenberg 被判犯有诈欺罪。
纽约的联邦陪审员週四(18日)认定 Avraham Eisenberg 因其在 2022 年 10 月 11 日的交易行为而犯有商品诈欺、商品操纵和电信诈欺罪,判决定於 7 月 29 日进行。他在电信诈欺罪上面临 20 年的监禁,在其他指控上分別面临 10 年监禁。
检察官指控自称为「应用博弈理论家」的 Eisenberg 使用假身份在 Mango Markets 上进行交易,拉抬了 Mango 原生代幣 MNGO 的价格以及永续期货合约,隨后利用该平台的一项允许他「借入」其持有的资產,提取了价值 1.1 亿美元的加密货幣,而他並无意偿还。据此前报导,Eisenberg 后来与 Mango DAO 协商,同意归还 6700 万美元的资金。
检方表示,Eisenberg「抬高」了 MNGO 代幣的价格,让他得以对 Mango Markets 实施其预谋数週的诈欺行为,「他打算拿了钱就跑」。判决后,Eisenberg 的律师 Brian Klein 在一份声明中表示:「我们显然很失望,但我们將继续为我们的客户而战。我们计划提出一系列审后动议。」
Klein 表示他的当事人执行了一个完全合法的策略,「完全遵守」控制 Mango Markets 的智能合约,该平台只对用户警告称「这是未经审计的软体,使用风险自负」。但美国助理检察官 Thomas Burnett 表示,Mango Markets 的平台规则並不能保护 Eisenberg 免受诈欺和操纵行为的起诉。
2024.4.17, Two people were arrested in Plano for an alleged gift card scheme involving several North Texas stores.
Plano police arrested Xiaohong Zhang and Xiongling Chen, both of California, last week in connection to the scheme.
California duo arrested in Plano for alleged ‘gift-card draining’ scheme
April 17, 2024
PLANO, Texas – Two people were arrested in Plano for an alleged gift card scheme involving several North Texas stores.
Plano police arrested Xiaohong Zhang and Xiongling Chen, both of California, last week in connection to the scheme.
Police say it’s a scam called “gift card draining.”
It involves scammers grabbing unpurchased gift cards from service kiosks and getting the card numbers and PIN codes.


Once the scammers get the information, they reseal the cards and put them back on the shelves.
Then, when someone buys a tampered card, the scammer drains all of the money from the prepaid card.
Plano police say they worked with the Secret Service and ICE to investigate the scam across the DFW area. Through surveillance, they say Zhang and Chen were seen placing tampered gift cards back in store Kiosks across several North Texas stores, including in Plano.
Plano police seized 4,100 tampered Apple gift cards valued at $649,000 in connection to the scheme.
“The Plano Police Department encourages the public to be vigilant when purchasing gift cards and to report any suspicious activity to the authorities,” the department said in a press release. “Consumers should inspect gift cards prior to purchase and notify staff if anything appears out of the ordinary. It’s also important to keep the receipt as proof of purchase.”
Anyone who thinks they bought a tampered gift card can contact the retailer where they bought it. They can also file a report with police and the FTC.
Zhang and Chen are each charged with unlawful use of a criminal instrument.
Police say more arrests are forthcoming.
—
盜刷65萬元 2加州華人德州落網
遭到逮捕的Xiongling Chen(左)與Xiaohong Zhang(右)。(科林縣監獄提供)
德州布蘭諾市警局近日逮捕兩名來自加州的華人,男的名為陳雄林(音譯,Xiongling Chen),女的是張小虹(音譯,Xiaohong Zhang),因為他們涉及德州北部多商店的禮物卡盜刷事件,兩人的罪名都是不法使用犯罪工具。
警方與特勤局(Secret Service)、移民局(ICE)合作,在達拉斯-福和市地區(Dallas-Fort Worth)追查「刷光卡片」(Gift Card Draining)的犯罪集團,逮捕兩人時起出4100張Apple禮物卡,總價達64萬9000元。警方說還有後續收網行動。
這類犯罪手法是,嫌犯先在店內取得還沒賣出的禮物卡,並取得卡號與PIN碼後,再還原包狀放回貨架。一旦有人買卡,歹徒就會先領光卡內金額。在跟監多日之後,警方確定陳男與張女在多家店內都有放回卡片的行為,因此逮捕兩人。
市警局呼籲,民眾購買禮物卡時應提高警覺,在使用前確認卡片沒有被動手腳,也應該保留購買收據,一旦發現可疑跡象就應向執法單位通報。認為自己可能賣到問題卡的民眾可以聯絡零售商,也可以向警方或聯邦貿易委員會(FTC)通報。
2024.4.15, Montrealer who stole millions with fake psychic fraud is sentenced to 10 years in U.S. prison
The U.S. Justice Department says Patrice Runner, 57, used a Montreal company to steal more than $175 million from 1.3 million people in the U.S. between 1994 and 2014.
PRESS RELEASE
Canadian Man Sentenced for Operating $175M Psychic Mass-Mailing Fraud Scheme
Monday, April 15, 2024
For Immediate Release
Office of Public Affairs
Scheme Defrauded Over 1.3 Million Victims in the United States
A Canadian man was sentenced to 10 years in prison today in the Eastern District of New York for perpetrating a massive psychic mass-mailing fraud scheme that stole more than $175 million from more than 1.3 million victims in the United States.
Following a two-week trial, a federal jury convicted Patrice Runner, 57, a Canadian and French citizen, in June 2023 of conspiracy to commit mail and wire fraud, conspiracy to commit money laundering and multiple counts of mail fraud and wire fraud.
Runner operated a mass-mailing fraud scheme from 1994 through November 2014. As part of the scheme, Runner sent letters to millions of U.S. consumers, many of whom were elderly and vulnerable. The letters falsely purported to be individualized, personal communications from well-known so-called “psychics” Maria Duval and Patrick Guerin and promised that the recipient had the opportunity to achieve great wealth and happiness with the assistance of the “psychics” in exchange for payment of a fee. Once a victim made a single payment in response to one of the letters, the victim was bombarded with dozens of additional letters, all purporting to be personalized communications from the “psychics” and offering additional services and items for a fee.
Although the scheme’s letters frequently stated that a “psychic” had seen a personalized vision regarding the recipient of the letter, in fact, the scheme sent nearly identical form letters to tens of thousands of victims each week. Runner and his co-conspirators obtained the names of elderly and vulnerable victims by renting and trading mailing lists with other mail fraud schemes. In reality, Duval and Guerin had no role in sending the letters, did not receive responses from the victims, and did not send the additional letters after victims paid money. In fact, no “psychics” played any role in Runner’s operation. Some victims made dozens of payments in response to the fraudulent letters, losing thousands of dollars.
Runner directed the scheme for the entirety of its twenty-year operation, directing co-conspirators, who ran the day-to-day operations of the scheme through a Canadian company. Runner used a series of shell companies registered in Canada and Hong Kong to hide his involvement in the scheme while living in multiple foreign countries, including Switzerland, France, the Netherlands, Costa Rica and Spain.
Spanish authorities extradited Runner to the United States to face federal charges in December 2020.
“This case demonstrates that the Justice Department’s Consumer Protection Branch and its partners in the U.S. Postal Inspection Service (USPIS) are committed to investigating and prosecuting transnational fraud schemes targeting Americans consumers,” said Principal Deputy Assistant Attorney General Brian M. Boynton, head of the Justice Department’s Civil Division. “The global nature of this scheme meant that we had to rely on law enforcement from around the globe to provide evidence of criminality. We want to thank officials from France, Liechtenstein, Switzerland and Canada, and in particular the Canadian Competition Bureau, for providing assistance in securing evidence in this matter, as well as Spain for arresting and extraditing Runner, ensuring that justice could be done.”
“Patrice Runner’s extravagant lifestyle, born on the backs of millions of older and vulnerable Americans, has come to an end,” said Inspector in Charge Chris Nielsen of the USPIS Philadelphia Division. “The conviction and federal sentencing of Patrice Runner is the appropriate punishment for someone who routinely preyed on vulnerable and elderly Americans. Postal Inspectors will continue to work tirelessly to ensure you can trust that the US Mail is free of these types of predatory schemes.”
Four other co-conspirators previously pleaded guilty to conspiracy to commit mail fraud in connection with this mass-mailing fraud scheme: Maria Thanos, 60, of Montreal, Canada; Philip Lett, 53, of Montreal; Sherry Gore, 73, of Indiana, and Daniel Arnold, 62, of Connecticut.
USPIS investigated the case.
Assistant Director John W. Burke and Trial Attorneys Charles B. Dunn, Rachel Baron and Ann Entwistle of the Civil Division’s Consumer Protection Branch prosecuted the case. The Justice Department’s Office of International Affairs provided critical assistance in securing Runner’s extradition.
The department urges individuals to be on the lookout for fraudulent “psychic,” lottery, prize notification and sweepstakes scams. If you receive a phone call, letter or email promising a large prize in exchange for a fee, do not respond. Fraudsters often will use official-sounding names or the names of real lotteries or sweepstakes, or pretend to be a government agent purportedly helping to secure a prize.
If you or someone you know is age 60 or older and has experienced financial fraud, experienced professionals are standing by at the National Elder Fraud Hotline: 1-833-FRAUD-11 (1-833-372-8311). This Justice Department hotline, managed by the Office for Victims of Crime, can provide personalized support to callers by assessing the needs of the victim and identifying relevant next steps. Case managers will identify appropriate reporting agencies, provide information to callers to assist them in reporting, connect callers directly with inappropriate agencies and provide resources and referrals, on a case-by-case basis. Reporting is the first step. Reporting can help authorities identify those who commit fraud and reporting certain financial losses due to fraud as soon as possible can increase the likelihood of recovering losses. The hotline is open Monday through Friday from 10:00 a.m. to 6:00 p.m. ET. English, Spanish and other languages are available.
—
Canadian con artist sentenced to 10 years for $175M psychic mail fraud in U.S.
Across 20 years, Canadian Patrice Runner conned over 1.3 million Americans out of more than US$175 million (more than C$241 million) by posing as a mail-in psychic — but his phony premonitions never anticipated a 10-year prison sentence in the U.S.
Runner, who previously lived in Montreal, was handed his 10-year sentence in the Eastern District of New York on Monday, according to a press release from the U.S. Department of Justice (DOJ).
The 57-year-old was convicted in June 2023. He was found guilty on 14 charges including conspiracy to commit mail and wire fraud, eight counts of mail fraud, four counts of wire fraud and conspiracy to commit money laundering.
Runner, who also possesses French citizenship, ran his psychic mail scheme alongside other co-conspirators from 1994 through November 2014. He sent letters to millions of Americans while pretending to be either Maria Duval or Patrick Guerin, both of whom are well-known “psychics.” (Duval and Guerin were not involved in sending the letters, the DOJ claimed.)
Runner’s fraudulent mail promised Americans an opportunity to “achieve great wealth and happiness with the psychic’s assistance, in exchange for payment of a fee.” Many of the letters claimed the psychic had seen a vision specifically about the recipient.
The DOJ said Runner’s scheme preyed specifically on victims who were “elderly and vulnerable.”
Nearly identical letters were sent to tens of thousands of victims each week.
Once Runner had a victim who took the bait, he and his co-conspirators would inundate them with dozens more letters, again claiming to offer personalized services or products for further payment.
“Some victims made dozens of payments in response to the fraudulent letters, losing thousands of dollars,” the DOJ wrote.
Then, after 20 years of leading the mail fraud operation, Runner was arrested in Ibiza in 2020.
He was extradited to the U.S. from Spain that same year.
In a 2023 interview with The Walrus, Runner maintained he’d never done anything illegal.
“Maybe it’s not moral, maybe it’s bulls—t,” he said. “But it doesn’t mean it’s fraud.”
Speaking from a New York detention centre, Runner said the “most lucrative years” for his scheme were between 2005 and 2010. He claimed to have once made US$23 million (over C$31 million) in a single year.
“I used to live like a rock star,” Runner said. “I was not cautious enough. I thought the mail-order business would be forever.”
“Patrice Runner’s extravagant lifestyle, born on the backs of millions of older and vulnerable Americans, has come to an end,” said Chris Nielsen of the USPIS Philadelphia Division. “The conviction and federal sentencing of Patrice Runner is the appropriate punishment for someone who routinely preyed on vulnerable and elderly Americans.”
“Postal Inspectors will continue to work tirelessly to ensure you can trust that the US Mail is free of these types of predatory schemes,” Nielsen promised.
Runner’s company ran its day-to-day direct-mail operations out of Montreal.
He and his co-conspirators gathered the names of elderly and vulnerable victims through a criminal circle renting and trading in mailing lists for the purpose of fraud.
To mask his scheme, the DOJ said Runner used a series of shell companies registered in Canada and Hong Kong.
While hiding from the law, Runner lived in countries including Switzerland, France, the Netherlands, Costa Rica and Spain.
Four of his co-conspirators have already pleaded guilty to conspiracy to commit mail fraud in connection to the scheme. Among them are Maria Thanos and Philip Lett, both from Montreal.
Before his arrest, Runner was found guilty and fined for orchestrating two other scams. One saw him falsely advertise a clairvoyant who could predict winning lottery numbers, and in another, Runner hocked phony weight loss products.
How to protect yourself from mail fraud
Canadians should be wary of any fraudulent lottery, prize notifications and sweepstakes scams that may arrive in the mail (or by phone).
Innovation, Science and Economic Development Canada, a government body that seeks to strengthen a fair marketplace, encourages citizens to deal with only registered companies or charities.
You should never trust unsolicited offers requiring your credit card number or banking information, or requests for you to call a 1-900 number.
Concerned Canadians can contact your provincial or territorial consumer affairs office or the Better Business Bureau to find out if the business is registered and if there have been any complaints against the company.
—
Montrealer who stole millions with fake psychic fraud is sentenced to 10 years in U.S. prison
The U.S. Justice Department says Patrice Runner, 57, used a Montreal company to steal more than $175 million from 1.3 million people in the U.S. between 1994 and 2014.
A former Montreal resident was sentenced earlier this week to 10 years in a United States federal prison for a multi-decade fraud that manipulated more than one million Americans into sending money to fake psychics.
Patrice Runner, 57, was convicted of 14 charges, including mail fraud and wire fraud, in June 2023 after a trial in a New York Federal Court.
Runner, a Canadian and French citizen, was found to have stolen more than $175 million from 1.3 million people in the U.S. between 1994 and 2014 by sending letters promising psychics would help them achieve wealth and happiness in exchange for a fee, the U.S. Justice Department said in a statement Monday.
In their sentencing recommendation, prosecutors said that on average Runner “defrauded more than 7,000 victims per week. Seven thousand victims would be notable in any case — but for Runner, that was only seven days’ work out of more than 20 years.”
“He did nothing else; he possesses no other skills. Runner was a full-time fraudster for decades.”
Runner used a Montreal company to send the letters to people across the U.S. and Canada. Each one claimed to be a personal communication from “so-called ’psychics’ Maria Duval and Patrick Guérin,” according to the Justice Department. However, no purported psychics were involved in the operation and the personalized letters were nearly identical forms sent to people whose names were obtained from mailing lists created by other con artists.
People who sent money would receive dozens of additional letters offering to sell them more services and items with supposed magical powers.
Prosecutors had sought a 30-year sentence for Runner, a former Montrealer, who directed the scheme from a number of countries before he was arrested in Spain, from where he was extradited to the U.S. in 2020.
“Runner took total advantage of his victims and their desperation, millions of times. Each of those more than six million victim payments represents a person reaching out for help that never came and that Runner never even tried to provide. Runner promised his victims easy, magical answers in exchange for a fee, and provided nothing in return except a cheap, fake trinket,” prosecutors wrote.
Runner’s defence lawyer had sought a five-year sentence, arguing that many of his client’s “customers” didn’t feel that they had been ripped off and that of those who did the vast majority lost no more than $40.
“The government has portrayed Patrice Runner as greedy, cynical, and heartless. He is none of those things,” James Darrow, an assistant federal defender, wrote in his sentencing recommendation.
“To be sure, the jury has determined that much of his astrological work was fraudulent. But it also determined that much was not. Hundreds of thousands of customers, hopeful for magic, came to Patrice Runner for astrological goods and service. Whatever one might say about Mr. Runner’s motivations, it is undisputed that he spent years trying to help them believe they were getting exactly what they wanted,” Darrow wrote.
The defence lawyer’s submission says that Runner, who grew up in an abusive home, used the money to give his children the stability and safety that he never had. Darrow also asks for leniency because of the conditions at the Metropolitan Detention Center, in Brooklyn, N.Y., where Runner has been held for more than three years. Darrow said Runner has become ill, deprived of medical care, held in near solitary confinement and denied the ability to meaningfully participate in his own defence.
Four of Runner’s co-conspirators — two Canadians and two Americans — pleaded guilty in 2018, though only one has been sentenced. Sherry Gore, 73, who prosecutors said managed a process to extract additional money from victims, received two years probation and a $1,000 fine in 2018.
Four people who ran PacNet Services, a British Colombia-based payment processing company used by Runner, and allegedly by other scammers, have been indicted in the state of Nevada by U.S. federal prosecutors, who are seeking their extradition from Canada.
—
通灵诈骗数亿美元 加国男子被判入狱10年
【2024年04月18日讯】(多伦多报导)加拿大男子、蒙特利尔前居民帕特里斯·兰纳(Patrice Runner),历时20年,诈骗金额数亿美元。近日,被美国联邦法院宣判,入狱10年。
根据美国司法部周一(4月15日)公布的公告,兰纳在1994至2014年的20年间,假借通灵者的名义,仅从130多万美国受害者处,就诈取了大约1.75亿美元。
2023年6月,兰纳在美国被判14项罪名成立,包括邮件诈欺和电汇诈欺。
兰纳的欺诈方式是寄信,承诺通灵者将帮助当事人获得财富和幸福,但当事人得付钱。
公诉人在量刑建议中提到,兰纳“每周诈骗7,000多名受害者,无论如何,这7,000多都引人注目”,而这只是他20年来7天期间所进行的诈骗。
57岁的兰纳通过蒙特利尔的一家公司把信件寄给美国和加拿大人。信中假借通灵者玛丽亚·杜瓦尔(Maria Duval)和帕特里克·盖林(Patrick Guerin)的名义,骗取钱财。
兰纳还在多个国家策划这种骗局,后来在西班牙被捕,并于2020年被引渡到美国。
据加通社报导,兰纳的四名同谋,两名加拿大人和两名美国人,已于2018年认罪,但只有一人被判刑。73岁的雪莉·戈尔(Sherry Gore)管理从受害者那里榨取额外金钱的渠道,在2018年被判处两年缓刑和1,000美元罚款。
卑诗省付款处理服务公司PacNet Services的四名经营者,受到美国起诉,美方正在寻求引渡。该服务公司不仅为兰纳,也为其他诈骗者提供服务;去年底,卑诗省充公了从该公司没收的的1,000万元诈骗赃款。
2024.4.16, Colorado funeral home owners accused of mishandling 190 bodies charged with Covid-19 relief loan fraud, officials say
疫情下的火葬詐欺:棄置190具遺體、偽造骨灰,美國殯葬夫妻檔被控重罪
Colorado funeral home owners accused of mishandling 190 bodies charged with Covid-19 relief loan fraud, officials say

The owners of a Colorado funeral home accused of mishandling nearly 200 sets of human remains are now facing charges for allegedly fraudulently obtaining more than $880,000 in Covid-19 relief funds and using it for personal expenses like trips and jewelry, federal prosecutors said.
Jon and Carie Hallford each face federal charges, including 13 counts of wire fraud and two counts of conspiracy to commit wire fraud, the United States Attorney’s Office for the District of Colorado said in a news release Monday.
The Hallfords are accused of using $882,300 in pandemic relief loans meant to help support small businesses on things like “a vehicle, multiple vacations, entertainment, dining, tuition for a minor child, cryptocurrency, cosmetic medical procedures, jewelry” and items from Amazon, an indictment filed in the US District Court of Colorado said.
A judge on Monday scheduled an arraignment for each defendant for Thursday, court records show. An attorney for Carie Hallford told CNN they have no comment. CNN reached out to the Colorado Public Defender’s Office for comment on behalf of Jon Hallford.
The Hallfords also face state charges related to the October discovery in of 190 sets of human remains improperly stored at their Return to Nature Funeral Home in Penrose, Colorado. The facility said it offered “green burials,” without embalming fluid, in a biodegradable casket or “none at all.” Their arraignments on those charges are scheduled for June 6.
Investigators were called to the funeral home after receiving a report of an odor coming from the building, Fremont County officials said at the time.
The Hallfords were arrested in November by the Colorado Bureau of Investigations on 190 counts of abuse of a corpse and counts of theft, money laundering and forgery, according to state charging documents.
They have not yet entered pleas for those charges.
The federal indictment alleges the pair defrauded their funeral home customers by not providing a cremation or burial for the deceased as promised.
“Beginning as early as September of 2019, and continuing through October of 2023, the Hallfords failed to cremate or bury approximately 190 bodies in connection with the scheme,” the indictment said. They allegedly “collected in excess of $130,000 from victims for cremation or burial services which they never provided,” prosecutors allege.
The Hallfords “concealed the gruesome collection of bodies … by preventing outsiders from entering their building, covering the windows and doors of the building to limit others from viewing inside, and providing false statements to others regarding the foul odor emanating from the building and the true nature of the activity occurring inside,” the indictment said.
The Hallfords each face up to 20 years in prison and up to $250,000 in fines if convicted in the federal case, according to the indictment.
Demolition of the funeral home is set to begin Tuesday, the US Environmental Protection Agency said last month.
“Following the assessment, EPA has determined that demolition of the building is necessary to safely remove all residual medical and biological materials found in the building. The cleanup will be conducted under the direction of EPA’s Emergency Response personnel and its trained hazardous materials contractors,” the agency said.
—
Colorado funeral home owners indicted again and back in jail — this time for alleged wire fraud
The married couple who own the Return to Nature Funeral Home in Penrose are back behind bars as the facility where nearly 200 “improperly stored bodies” were discovered last fall will be demolished. Jon Hallford and Carie Hallford have been arrested by the FBI and indicted by the federal government for allegedly defrauding customers and the government.
The Hallfords have each been charged with 10 counts of wire fraud over their alleged failure to bury or cremate bodies of people, despite taking money for the services. They’ve also been accused of making false statements to the U.S. Small Business Administration in their efforts to qualify for three separate loans totaling $882,300.
“Beginning as early as September of 2019, and continuing through October of 2023, the Hallfords failed to cremate or bury approximately 190 bodies in connection with the scheme. As a result, the Hallfords collected more than $130,000 from victims for cremation or burial services which they never provided,” the 19-page federal indictment filed last week reads.
The two appeared in federal court Monday to hear the charges against them. Among the allegations are that they defrauded the government to obtain SBA loans during the pandemic by defrauding the Paycheck Protection Program, which is part of The Coronavirus Aid, Relief, and Economic Security (CARES) Act, obtaining $882,300. The indictment indicates they spent money improperly on, “a vehicle, multiple vacations, entertainment, dining, tuition for a minor child, cryptocurrency, cosmetic medical procedures, jewelry, various goods and merchandise from Amazon, and payments to other vendors unrelated to their business.”
“That’s scamming all of us,” said Abby Swoveland.
The body of her mother Sally was among those found in the building.
“We are all paying that. I am glad he is going to be answering to that. And she is, too”
Swoveland has had a long and difficult six months.
“There was a tremendous amount of shame that I had to work through on my own because I picked them, I chose them and this is what they did,” she explained.
She has been an advocate of changing requirements for funeral home operators and on inspections in the Colorado Legislature.
“And so speaking out had helped me with that.”
Plans to tear the building down are a positive to her, “I think it’s great. It’s a long time coming. It’s time for that building to go. That is going to be I think a cathartic moment for many, many families.”
The funeral home grounds are set to be demolished this week after a ceremony for families of those impacted on Tuesday morning. The process is expected to take about 10 days to complete.
In the latest indictment, the Hallfords are facing 13 counts of wire fraud and aiding and abetting and two additional counts of conspiracy to commit wire fraud. If convicted, they could face up to 20 years in federal prison, up to a $250,000 fine — or a combination of the two — up to 3 years of supervised release and they could be ordered to pay restitution.
The Hallfords are also facing hundreds of charges in connection to the Return to Nature Funeral Home including abuse of a corpse, forgery and money laundering. The couple was arrested in Oklahoma in November 2023.
It was last fall when 190 improperly stored bodies were discovered inside the Return to Nature Funeral Home. The investigation into the funeral home began in early October 2023 when neighbors reported a foul smell to law enforcement.
All decedents were removed from the funeral home on Oct. 13, 2023 and transported to the El Paso County Coroner’s Office. In February, Gov. Jared Polis issued a second Executive Order to provide an additional $220,000 for DNA testing related to the funeral home investigation. Fremont County Coroner Randy Keller said this week that 18 bodies have yet to be identified.
Swoveland and other families hope that the Hallfords face vigorous prosecution as they hope to put this painful chapter behind them, “That’s all we’ve got at this point to hold onto. The victims are just wanting justice. We all want justice. And we all want to see the Hallfords to answer for what they did.”
—
疫情下的火葬詐欺:棄置190具遺體、偽造骨灰,美國殯葬夫妻檔被控重罪
「你本是塵土, 仍要歸於塵土……」美國科羅拉多州2023年爆出大規模「火葬詐欺案」,一家殯儀館數年來收了錢卻沒有火化遺體,不僅偽造證明、給家屬裝有假骨灰的骨灰罈,還將騙來的費用都花在奢侈消費。檢警在當地空屋找到高達190具腐爛遺體,有些至少被棄置4年之久。殯儀館經營者霍爾福夫妻在今年4月15日被控200多項罪名,最高可能判處20年徒刑。主要犯案期間正值疫情高峰,火葬數量攀升、葬禮從簡成為趨勢,卻讓該殯儀館有機可趁,也凸顯該州殯葬法規監管不力。而數百個家庭好不容易從送別親人的悲痛中走出,卻又面臨摯愛遺體毀損、甚至不知所蹤的情況,留下無盡不解與創傷。
2023年10月初,美國科羅拉多州科羅拉多泉市爆出「回歸自然殯儀館」(Return to Nature Funeral Home)火葬詐欺案。法院在4月15日公開起訴文件,經營者霍爾福夫妻喬恩與凱莉(Jon and Carie Hallford)面臨250多項指控,包含190起虐待遺體罪(abuse of a corpse)、5起竊盜罪、4起洗錢罪以及至少50起偽造文書罪等等。檢察官指控夫妻倆不僅沒有依照程序處理遺體,還將至少90萬美元的葬禮費用與疫情紓困金全數花在度假、醫美手術等奢侈用途。
▌大型鑑識團隊出動
根據《美聯社》調查,霍爾福夫妻將本應火化的遺體藏在鄰近的彭羅斯鎮(Penrose),這是個不到4,000人的小鎮,多數居民通勤到科羅拉多泉市上班。2023年10月初,鎮上民眾檢舉當地一棟建築傳出臭味,檢警循線尋獲被棄置的遺體。由於數量太過龐大,科羅拉多州州長波利斯(Jared Polis)還為此發布了口頭災難聲明(verbal disaster declaration),州政府災難應變單位以及3個郡的驗屍官都被動員,連國土安全局(Homeland Security)、聯邦調查局(FBI)都派員參與調查、鑑識和清理,這類團隊通常僅在空難等大型災難才會出動。
FBI探員柯恩(Andrew Cohen)在法庭作證表示,當他們走進藏有遺體的房屋,連身經百戰的鑑識人員都感到心驚。屋內沒有任何冷藏或冷卻設備,遺體如同貨物般層層疊疊,地上屍水累積好幾吋深,大門已透出一個大大的污漬,蒼蠅與蛆蟲更是滿佈整間屋子。柯恩指出,至少可以確認有23具遺體死於2019年、61具遺體死於2020年,當中包括成人、嬰兒與胚胎。
柯恩心有餘悸地說:「那是你會想要忘掉的畫面,但忘不掉。」
時間過去逾5個月,鑑識單位仍在盡力透過DNA、指紋、牙科紀錄或金屬關節等醫療植入物來辨識死者身分。陸續確知身分後,調查單位也一一聯絡家屬,很多人直到接獲通知才知道親人的遺體被棄置到腐爛。有些家屬則是看到新聞後向火化場確認,卻崩潰發現火化證明根本是偽造的,這代表許多家屬當初拿到的骨灰可能不是「自家人」。
根據法務部網站解釋,經焚化爐妥善火葬後的屍骨當中,所有有機體的DNA分子結構已被高溫破壞,所以無法再進行DNA檢驗。這也意味著,如果家屬發現自家親人的遺體尚未火化,很可能永遠無法查出家裡那罐骨灰究竟屬於何者。此外,至少4位死者的家屬也懷疑自家骨灰罈裡裝著「水泥」。當中有2位家屬「敢於求證」,他們拿水混和之後,發現「骨灰」竟然真的凝結成塊。後續調查也顯示,2020至2023年間,霍爾福夫妻從賣場購買了高達600磅(約272公斤)的水泥,可能就是用來偽裝成骨灰。
除了火葬案件之外,FBI還發現其中一具遺體屬於一名前陸軍三等士官長,但該士官長當初舉行的是土葬。調查人員與家屬挖開墳墓後,赫然發現棺材裡躺的是一具女屍。該名士官長已重新舉行軍葬禮並下葬於軍人公墓。檢調此次至少發現2起「埋錯屍體」的情況,但並未披露被錯埋的遺體身分,也不清楚怎麼會發生這種事。
上述種種離譜的發現,引發許多遺屬的震驚與悲痛。福特(Stephanie Ford)表示,丈夫衛斯理(Wesley Ford)生前強調他討厭棺材,因而選擇火化,殊不知丈夫成為被棄置的遺體之一。她在受訪時失聲痛哭:「我知道這不是我的錯,但還是會有罪惡感…我讓他失望了。」威爾森(Tanya Wilson)則在2022年8月依照媽媽遺囑將骨灰撒在夏威夷海裡,警方卻告訴她,她媽媽的遺體自始至終都躺在那棟空屋裡。威爾森表示:「我們以為完成了她的心願,結果我們獲得的所有平靜都被剝奪了。」她也自陳會不斷幻想,母親的遺體如何被堆疊在滿是屍水的陰暗房間裡,深陷在痛苦的想像裡。
另一位母親佩姬(Crystina Page)更在Facebook設立專頁,號召受害家庭團結發聲。佩姬20歲的兒子大衛(David)在2019年被執法單位射殺身亡。佩姬自此投身警界改革的倡議行動,過去4年都抱著兒子的骨灰罈東奔西走,這個紅色骨灰罈陪著佩姬去到科羅拉多州議會、甚至還去過華府,豈知裡面裝的根本不是大衛。
佩姬說:「我兒子就在那裡躺了4年,靜靜腐爛……我這輩子從來沒有過這麼糟的感受。」
▌事跡敗露
整起事件敗露的起點,源自霍爾福夫妻因欠稅而遭驅離,似乎早已面臨嚴重財務危機。曾與殯儀館配合的威爾伯火化場(Wilbert Funeral Services)表示,雙方早在2022年年底終止合作,但殯儀館積欠火化費用將近一年,火化場忍無可忍告上法院,才導致司法介入。但殯儀館在這段期間仍然向外界假裝正常營業,繼續收受遺體、舉辦葬禮,還開立假的火化證明給家屬。《美聯社》記者檢視了部分家屬提供的火化證明,許多日期都是在停止與火化場合作之後。
起訴書指出,從未舉行的火葬和土葬儀式至少為霍爾福夫婦賺進13萬美元,他們還申請了至少3筆貸款與高達88萬2,300元的疫情紓困金,卻不是拿去付清欠款。柯恩探員證稱,霍爾福夫妻花了12萬美元買了一台GMC Yukon大型休旅車和一台日產豪華轎車Infiniti,光是這筆費用就足以付清近400具遺體的火葬費,他們卻選擇任由那190具遺體自行腐爛。夫妻倆也將財產花在孩子的學費與醫美手術等等,購買了逾3萬美元的加密貨幣,還有古馳(Gucci)與蒂芙尼(Tiffany & Co)等名牌精品。
本案另一項疑點之一在於,近200具遺體為何沒有更早引發惡臭或其他衛生問題?但根據《衛報》調查,早在2020年時政府單位曾就接到投訴,有人指控殯儀館「不當存放遺體」,當局僅僅打了一通電話查問,霍爾福夫妻宣稱臭味是來自剝製標本,逃過一次調查機會。而霍爾福夫妻是否有對遺體進行任何除臭處理?抑或躲過了哪些調查與投訴?因為倆夫妻與律師至今不肯接受任何媒體訪問,也還未開始在法庭上答辯,外界仍無法得知更多犯案細節。
不過,媒體調閱法庭證據發現,霍爾福夫妻早在2020年就已開始擔心事跡曝光,討論該如何解決掉眾多遺體。檢察官克拉克(Kevin Clark)在法庭公布兩人簡訊,喬恩曾傳訊給妻子表達擔憂:
「選項A,盡快蓋一個新機器;B,挖個大洞,再倒入鹼液(lye),但要在哪?C,挖個小洞放把大火,但要在哪?D,我去坐牢。這很有可能發生。」
再隔一年,喬恩仍在擔心遺體處置問題,但同時還能思考晚餐吃什麼。他再次於簡訊提到:
「我回家要馬上洗澡,剛剛搬運的時候我被『人汁』(people juice)噴到了。我要吃雙倍起司堡、加生菜、不要番茄,謝謝。」
但最令家屬遺憾、不解的是,霍爾福夫妻儘管擔憂被抓,卻沒有證據顯示他們採取任何實質行動來處理日益腐爛的遺體。長達3、4年的時間,霍爾福夫妻唯一的行動就是這些流露擔憂的簡訊。
▌為何沒被發現?
此案也暴露出,科羅拉多州的殯葬法規過度寬鬆,缺乏實際監督並存在許多漏洞。例如,回歸自然殯儀館的執業登記2022年11月就已過期,卻沒有任何人去檢查或提醒;而且這並非該州第一次發生「水泥冒充骨灰」案件,2023年1月也有一對母女被控沒有依約火化遺體,兩人分別被判20年與15年徒刑。本案爆發後,科羅拉多州去年底也通過新法,讓政府人員不需經過允許就能稽查殯葬單位,但州政府仍然沒有撥出更多預算來支援稽查行動,新規定形同虛設。
根據回歸自然殯儀館Instagram帳號,該館創立於2017年,主打「環保葬」(Green Burial)服務。美國傳統葬禮會為遺體進行防腐處理,以便來賓瞻仰遺容後再行下葬。但近年來隨著地價高漲、物價升高及環保觀念興盛等因素,愈來愈多人選擇不為遺體防腐,棺木也選用易生物降解的材質等。愈來愈多家屬也選擇先火葬,骨灰再採取樹葬、海葬等環保方式,甚至將骨灰罈放在家中緬懷。
不過或許我們仍會出現另一層疑惑,為什麼有這麼多家屬不知道骨灰罈裡裝的是「誰」?或許只能從不同的殯葬文化去理解。台灣普遍的葬禮流程中,告別式之後會直接移靈至火化場,家屬通常會看著逝去親人被推入火化爐,在2小時內完撿骨並拿回骨灰。但美國的火化流程則視家屬而定,看著遺體火化並非預設選項。如果不進行瞻仰儀式,通常會將遺體直接從醫院、家中或安養院運送到火化場,經安排火化之後,火化場員工再將燒完的骨頭碎片磨成細粒狀,由專人或快遞送還給家屬,告別式則是任何時間都能舉辦。因此,家屬確實很可能沒有仔細看過骨灰罈內容物。
而在2020年爆發的COVID-19疫情,更加速推高了火葬趨勢。3年多的疫情造成美國將近120萬人死亡,醫療機構與喪葬機構的量能都一度面臨崩潰,人們被迫不再遵守特定喪葬儀式。例如在疫情初期病毒傳播力仍然很強,染疫患者的遺族不但不能觸碰其遺體,為了安全起見,遺體還要盡速火化;而在火化場吃不消的情況下,許多遺體也被快速掩埋;此外染疫者的遺體使用特製納體袋收容,無法見上最後一面;有些患者死亡時還與家屬分隔兩地,只能立刻火化,種種情況可能都讓家屬難以確認親人遺體的最後下落。
從4月16日開始,聯邦環境保護局展開至少1周的拆除作業,預計將儲藏遺體的房屋夷平。所有遺骸在去年10月13日已經移到其他地點,驗屍官凱勒(Randy Keller)表示鑑識工作仍在持續,目前剩下18位死者尚未確認身分。民眾與家屬也在拆除工作開始之前舉行了一場悼念儀式。凱勒說:「希望儀式能畫下某種句點,為這起恐怖事件的相關受害者帶來一點點撫慰。」
回過頭來,霍爾福夫妻其實早在2019年就開始犯下虐待遺體與詐欺之罪,只是2020年COVID-19疫情大爆發,很大程度上延緩了其罪行被發現的時間,甚至因為社會整體對火葬的接受度變高,可能導致更多人因此受害。然而回歸自然殯儀館遠非個案,科羅拉多州立法與行政部門的怠惰,或許是更值得受到究責與追問的一方。
鑒於本案仍在進行中,法庭上將檢視更多待解的疑問。例如,如此大量的遺體未處理,殯儀館員工應當知情,為何沒有作為?又或者,土葬儀式將遺體調包又是為了什麼原因?諸多問題唯有在霍爾福夫妻配合下,才有機會獲得詳細解答。但無論如何解釋,殯儀館經營者何以能夠一邊安慰家屬、一邊對遺體棄之不顧,而過往還有多少家庭的摯愛親人也遭受這等待遇,恐怕會是受害家屬與數千鎮民心中永遠難以理解的結。
2024.4.16, 81-year-old charged with murder of Uber driver he mistakenly believed was a scammer, police say
据克拉克县治安官办公室称,一名 81 岁的俄亥俄州男子因误认为一名 Uber 女司机与骗子合作并试图敲诈他而开枪射击,因此被控谋杀罪。
81-year-old charged with murder of Uber driver he mistakenly believed was a scammer, police say

An 81-year-old Ohio man is charged with murder after he shot a female Uber driver he mistakenly believed was working with a scammer and attempting to extort him, according to the Clark County Sheriff’s Office.
William Brock shot Loletha Hall several times outside his South Charleston home on March 25, according to a criminal complaint. Hall was taken to a local hospital where she died.
Brock told police that prior to the shooting he had received threatening phone calls from a male caller who claimed one of Brock’s relatives was being held in jail, according to a news release from the sheriff’s office.
The caller then asked Brock to wire money for the relative’s bond, and when Brock resisted, the caller began threatening to harm him and his family.
When 61-year-old Hall arrived in her Uber at Brock’s residence, he shot her multiple times, the release states.
Brock believed Hall had a connection to the scam caller and would kill him and his family, according to a 911 call he made after shooting her, authorities said.
Police released dashcam video obtained from Hall’s vehicle of Brock confronting her outside his home.
‘A horrific tragedy’
Hall received a request on the Uber app to pick up a package from Brock’s residence, the news release states. Authorities believe she was “unfamiliar with the circumstances” surrounding the request.
Hall arrived in her Uber, and dash cam video from her car shows her getting out of the car to speak to Brock.
According to the news release, she made no demands of Brock other than to ask about the package she was sent to retrieve.
Brock was arrested and charged with murder as police saw no active threat presented by Hall during the encounter, and Brock failed to contact authorities for assistance, the sheriff’s office said.
Brock pleaded not guilty to a charge of murder and posted his $200,000 bond on Wednesday, according to court documents.
CNN has reached out to Hall’s family and to Brock’s defense attorney, Paul Kavanagh, for comment.
Uber has been in contact with Hall’s family and law enforcement, the company said. “This is a horrific tragedy and our hearts continue to be with Loletha’s loved ones as they grieve,” an Uber spokesperson said in a statement to CNN.
“We have been in contact with law enforcement and remain committed to supporting their investigation.”
Uber has banned the account of the individual who ordered Hall’s Uber to Brock’s house, the company said. Authorities believe that individual was either the original scam caller or an accomplice, according to the release.
The company says it’s committed to the safety of Uber drivers and has developed safety features including an in-app emergency button, route sharing features and the ability to connect to a live safety agent.
It’s unclear if authorities have identified the owner of the account or made any additional arrests.
CNN has reached out to the Clark County Sheriff’s Office for more information.
—
Uber driver shot and killed by 81-year-old Ohio man after both received scam calls, police say
An 81-year-old Ohio man has been charged with murder after allegedly shooting an Uber driver who thought she was picking up a package from the man’s house. Both appeared to have been victims of scam phone calls, the Clark County Sheriff’s Office said in a news release.
The Uber driver, Loletha Hall, was found shot multiple times near 81-year-old William Brock’s South Charleston home on March 25. Brock, who had called 911, had an injury to his head and ear and was bleeding when police arrived, according to a police report.
Hall, a Black woman, was taken to a hospital in Dayton, where she died of her injuries.
Investigators discovered that Brock had earlier received a scam call about an incarcerated relative, which had involved threats and demands for money.
An unknown man told Brock over the phone he needed to pay $12,000 to get his nephew out of jail, according to a police report. Brock told police the caller threatened to kill him and his nephew if he didn’t pay the ransom, the report said.
The same caller, or an accomplice, later hired Hall using the Uber app to pick up a package from Brock’s residence, according to investigators. Hall was not aware that Brock had been threatened, the sheriff’s office. said.
“Ms. Hall, suffering from medical conditions and unarmed, made no threats or assaults toward Mr. Brock, and made no demands, other than to ask about the package she was sent to retrieve,” the sheriff’s office said.
Brock allegedly held Hall at gunpoint and demanded to know the identities of the people who had called him. He also took Hall’s phone and refused to allow her to leave, officials said, adding that Brock did not try to call police at this point.
When Hall tried to get back into her vehicle, Brock allegedly shot her, and there was a “subsequent scuffle at the door of Ms. Hall’s vehicle,” the sheriff’s office said. Brock then allegedly shot her two more times, before calling 911.
Brock is charged with murder, which carries a penalty of 15 years to life in prison, court records showed. Police are considering other charges. Brock pleaded not guilty, and bail was set at $200,000, court records showed.
Officials are still searching for the scam callers.
“The Clark County Sheriff’s Office would like to take the opportunity to again remind residents, especially our older citizens, that no Law Enforcement Agency or Court will make contact with anyone in the manner of this case to solicit cash for bail,” the office said, urging residents “to use extreme caution when being contacted unexpectedly by subjects claiming to be relatives incarcerated in a correctional facility.”
2024.4.10, East Hampton Police say two New Yorkers were arrested last week after an investigation revealed they allegedly scammed an East Hampton resident out of more than $100,000 in gold.
2 charged with scamming East Hampton man out of $100K in gold

美國紐約州(New York)2名華人男子被提告盜竊罪。
EAST HAMPTON, Conn. (WTNH) – East Hampton Police say two New Yorkers were arrested last week after an investigation revealed they allegedly scammed an East Hampton resident out of more than $100,000 in gold.
According to police, the resident was scammed by someone who identified himself as a Homeland Security agent who claimed to be collecting a debt the victim owed, in gold.
The fraudulent agent set a time during with the gold would be picked up at the victim’s home.
While undercover at the victim’s home on the morning of April 4, the officers apprehended the suspects.
Fei Fei Jiang, 29, of Queens, New York, and Ya Lou Wang, 36, of Flushing, New York were both charged with first-degree larceny and first-degree conspiracy to commit larceny.
Neither suspect was able to post his bond- Jiang’s was $500,000 and Wang’s was $750,000. Both suspects appeared at the Middletown Superior Court on April 5, according to police.
Police said they were able to recover and return the victim’s more than $100,000 in gold.
—
假冒國安部人員騙價值10萬黃金 紐約2華裔非法移民被捕
美國紐約州(New York)2名華人男子,日前謊稱是國土安全部人員,在康乃狄克州(Connecticut)試圖騙取價值10萬元以上的黃金,遭到警方逮捕,指控兩項一級盜竊罪。據悉,兩人都是無證移民,案件仍在調查中。
康乃狄克州電視台《WTNH》報導,居住在紐約州皇后區59街的29歲男子蔣飛飛(Fei Fei Jiang,音譯),和居住在法拉盛的36歲男子王亞樓(Ya Lou Wang,音譯),近日來到康州度假時,謊稱是國土安全部人員,欺騙一位民眾他欠下一筆巨額債務,需用價值10萬元黃金償還,並和對方約定取款時間。
康乃狄克州東漢普頓(East Hampton)警方接獲報案,4日上午8時30分左右來到受害者住所附近進行臥底行動,在兩名華人男嫌前來取款時,當場將他們逮捕。
調查發現,兩人都是無證移民,被提告一級盜竊罪(first-degree larceny)和共謀犯一級盜竊罪(conspiracy to commit first-degree larceny),保釋金分別為50萬美元和75萬美元,由於兩人都無力支付,目前被關押在哈福特懲教中心(Hartford Correction Center)。
—
假冒国土安全部特工诈骗黄金 纽约两华男康州被捕
两名住在纽约市王后区的华人男子冒充国土安全部(DHS)特工,企图诈骗一名康州居民价值10万美元的黄金,4月4日遭到康州警方逮捕。
这名康州东汉普顿(East Hampton)居民日前接到一名自称国土安全部特工的男子的通知,称该居民欠了一大笔债务,需要用黄金偿还,并约定时间要到居民家中来取。4月4日上午8点30分,两名华男上门时被卧底的警察逮捕。警方调查后,将价值超过10万美元的黄金归还给该居民。
两名被捕的华男分别为:现年29岁、住在王后区的江飞飞(Fei Fei Jiang,音译)和现年36岁、住在法拉盛的王亚楼(Ya Lou Wang,音译),他们都是无证移民,被控犯有一级窃盗罪和共谋一级窃盗罪。两人于4月5日在米德尔敦(Middletown)高等法院过堂,江飞飞的保释金定为50万美元,王亚楼的保释金定为75万美元,两人都无法缴纳,继续还押。
2024.4.12, Riverside deputies arrest ‘fake priest’ wanted across the U.S.
Riverside deputies arrest ‘fake priest’ wanted across the U.S.
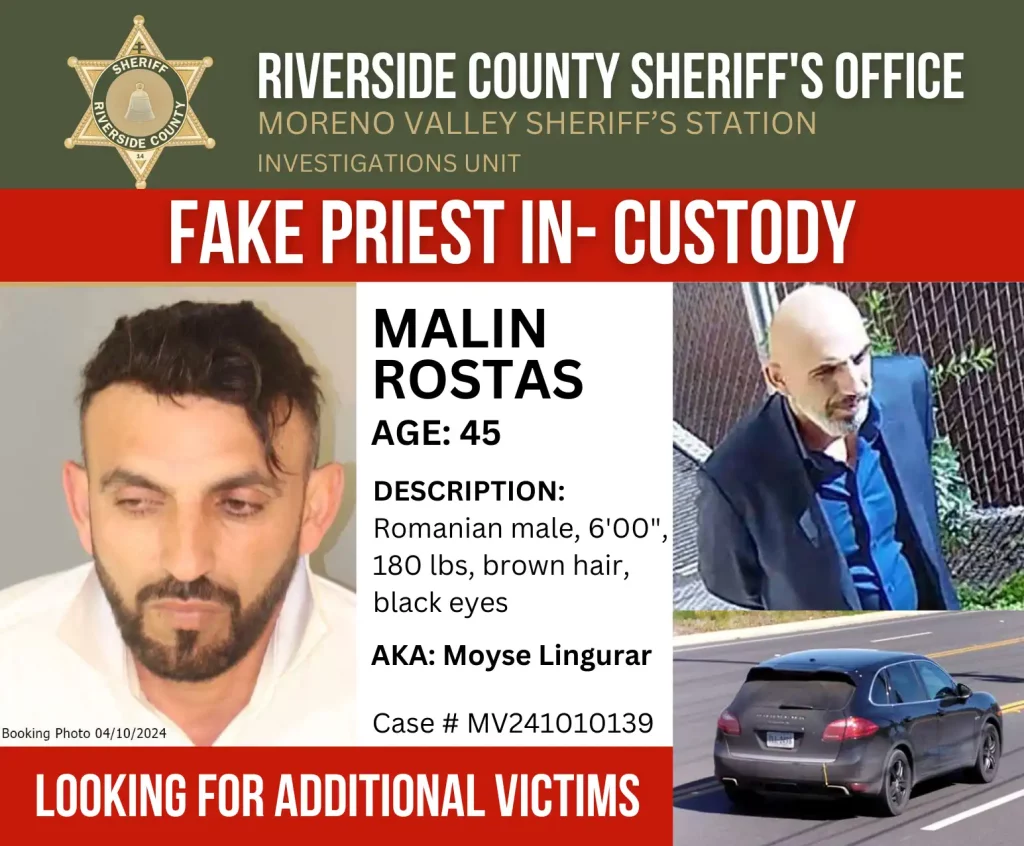
羅斯塔斯被指控冒充「馬丁神父」搶劫天主教堂。河濱縣警局
Deputies in Moreno Valley say they’ve arrested a “fake priest” wanted by authorities across the country.
Various law enforcement agencies across the U.S. have been on the lookout for 45-year-old Malin Rostas, who also goes by the name Moyse Lingurar.
He’s accused of posing as a priest, calling himself “Father Martin,” and using deception to steal from churches.
On Wednesday, Riverside County Sheriff’s Department deputies in Moreno Valley located a vehicle on the 10000 block of Pigeon Pass Road that matched the description of the one used by Rostas.
The driver identified himself as Father Martin, and the Sheriff’s Department said he had just attempted to steal from a local church.
Rostas, a New York resident, was taken into custody and booked into the Robert Presley Detention Center in Riverside on an outstanding felony warrant out of Pennsylvania.
Additional charges are expected to be filed for the attempted burglary in Moreno Valley, officials said.
The Riverside County Sheriff’s Department believes there may be additional burglary victims. Anyone with information regarding this case or similar cases is encouraged to contact the Moreno Valley Sheriff’s Station at 951-486-6700.
—
詐騙盜竊全國通緝 「假神父」南加落網
南加州內陸執法單位宣布一名經全國通緝、在各地教會盜取現金的「假神父」終於在莫雷諾谷落網。
《洛杉磯時報》報道,河濱縣縣警局指出,一名臭名昭著的假神職人員在全國各地教會進行詐騙竊盜,他最終在河濱縣被捕及面臨審判。
調查人員指出,幾個月來,被指控自稱「馬丁神父」的羅斯塔斯(Malin Rostas)穿著黑色服裝,出現在美國和加拿大各地天主教堂,自稱是「來自芝加哥的訪問神父」。
但調查人員表示,當信任他的東道主將他獨自留在教堂旁的私人住所時,羅斯塔斯便會趁機搜刮貴重物品,然後夾帶現金匆忙逃逸。
3月,紐約皇后區美國烈士羅馬天主教堂的雷達爾(Peter Raydar)神父遭盜九百元,他說:「他是一隻禿鷹,來到神聖教會行騙並侵犯所有人,這是非常可悲。」
雷達爾坦言,羅斯塔斯事前已做足功課,知道教會內人員的名字,他能使用教會詞彙,知道在何處能找到有價值的物品。
羅斯塔斯被指控在休士頓的一座教堂犯下類似罪行,據稱騙取五百元。當局表示,懷疑他從俄勒岡州一座教堂盜竊1700多元。
去年10月,斯托克頓教區也曾發出警告,聲稱兩名男子冒充墨西哥托盧卡真牧師的身份,向多數移民教區居民收取高昂費用,以進行即興儀式:洗禮、堅信禮、第一次聖餐。
正如教區發言人向《國家天主教紀事報》所描述的那樣,「披著羊皮的狼」甚至開始要求教區居民提供出生證明副本,引發教友對身份盜竊和可能人口販運的擔憂。
邁阿密教會官員近期警告信徒,假神職人員偽裝進行虛假儀式,以換取蓄有現金的iTunes禮品卡,一名教友被騙1500元。
類似詐騙情況變得猖獗,迫使當地大主教不得不在電視上發言提醒,儘管神父在彌撒期間傳遞募捐盤索情況很常見,但沒有天主教牧師會向教區教友索要禮品卡。
最近一起牧師騙局則發生在沙加緬度,當時一間小型快餐店連鎖店因違反勞動法而受到聯邦調查,店主曾僱用一名假神父來聽取員工認罪。該名假神父沒有讓員工審視靈魂並反思罪惡,而是不斷地將談話引向她的工作表現:詢問是否遲到、從餐廳偷過東西或做了任何傷害雇主的事情。
河濱縣警局表示,他們注意到羅斯塔斯的汽車與一系列入室盜竊案中所使用的車輛描述相符,最終發現45歲的紐約人羅斯塔斯是可疑車輛駕駛,在針對逮捕令進行例行檢查後,很快意識到面對的是被全國通緝、被指控為小偷的「假神父」。
羅斯塔斯因在賓州未執行的重罪逮捕令而遭關押在河濱市的羅伯特普雷斯利拘留中心。據治安部門指出,執法單位預計很快會對他提出更多的指控。洛杉磯訊
羅斯塔斯被指控冒充「馬丁神父」搶劫天主教堂。河濱縣警局
—
Nationwide manhunt for a fake priest who stole faith as well as cash ends in Moreno Valley
A notorious fake priest who left a trail of doubt and disbelief among the faithful he’s accused of swindling from coast to coast will soon face judgment in Riverside County, sheriff’s officials say.
For months, Malin Rostas, accused of calling himself “Father Martin,” allegedly donned black garb and showed up at Catholic churches across the U.S. and Canada claiming to be “a visiting priest from Chicago,” according to investigators.
But when his all-too-trusting hosts would leave him alone in the rectory — a priest’s personal quarters next to the church — investigators say Rostas would rifle through their valuables and make a hasty exodus with their cash.
In March, Father Peter Raydar, of the American Martyrs Roman Catholic Church in Queens, N.Y., got burned for $900.
“He’s a vulture, he’s a vulture,” Raydar told a local TV station. “It’s very sad that someone is going to come to any house of worship and just violate everybody.”
But, Raydar confessed, the alleged fake priest had done his homework. He’d learned the names of people at the church, used ecclesiastical vocabulary and knew where to find the loot, he said.
Rostas is accused of pulling a similar caper at a church in Houston, allegedly making off with $500. And authorities say they suspect him in the theft of more than $1,700 from a church in Oregon.
There’s nothing new about diabolical scammers posing as men of the cloth, of course.
In October, the Diocese of Stockton issued a warning about two men who had assumed the identities of real priests in Toluca, Mexico, and were charging mostly immigrant parishioners exorbitant fees to perform impromptu rituals: baptisms, confirmations, first Communions.
The “wolves in sheep’s clothing,” as a diocese spokeswoman described the men to the National Catholic Register, also started demanding copies of the parishioners’ birth certificates, raising fears of identity theft and possible human trafficking.
In Miami, church officials recently warned the faithful about fake priests performing bogus rituals in exchange for iTunes gift cards loaded with cash. One parishioner was duped for $1,500.
It got so bad, the local archbishop had to go on TV and remind his flock that, although it is common for priests to pass around the collection plate asking for money during Mass, “no Catholic clergyman will ask a parishioner for a gift card.”
But perhaps the most inspired recent priest scam occurred in Sacramento, when the owners of a small chain of taquerias that was under federal investigation for labor law violations hired a fake father to hear employees’ confessions.
“I found the conversation to be strange and unlike normal confessions,” one of the servers later told investigators.
Instead of giving her space to search her soul and reflect on her sins, the fake priest kept steering the conversation to her job performance: asking if the server ever showed up late, stole from the restaurant or did anything to harm her employer.
For “Father Martin,” the reckoning arrived Thursday morning in Moreno Valley in the form of Riverside County sheriff’s deputies who said they noticed his car matched the description of a vehicle used in a string of burglaries.
Behind the wheel they found Rostas, 45, of New York. After running a routine check for arrest warrants, they quickly realized they were face to face with what so many had been searching for — the man accused of being the pilfering padre.
Rostas was booked at the Robert Presley Detention Center in Riverside on an outstanding felony warrant from Pennsylvania. More charges are expected to be filed soon, according to the Sheriff’s Department.
2024.4.9,紐約長島再現電信詐欺案 2華人嫌犯遭逮捕。經調查,納蘇郡警察局逮捕了來自皇后區的47歲陳榮(Rong Chen,音譯)和來自賽奧塞(Syosset)的46歲余振生(ZhenSheng Yu,音譯)。他們均被提告重竊罪,並已於近日受到審訊。
據悉,近來在紐約周邊地區發生多起類似案件。上月,一名來自長島谷流(Valley Stream)的67歲老人,在發現電腦出現技術問題,撥打一位「技術代表」的電話,並向這位技術代表支付3萬2500元現金以期解決問題,警方隨後逮捕了報住在曼哈頓的43歲黃維序(Weixu Huang,以下均為音譯)和報住在布碌崙(布魯克林)的41歲游永梅(Yongmei You)。
紐約長島再現電信詐欺案 2華人嫌犯遭逮捕
紐約長島納蘇郡(Nassau County)近日逮捕2名涉嫌電信詐欺老人的華裔男嫌,金額超三萬元,2人都被提告重竊罪(Grand Larceny),警方提醒民眾對此類詐騙提告警惕。
根據警方,今年1月,一名來自納蘇郡馬鞍石(Saddle Rock)的83歲男性受害者在電腦上收到一則設備遭到破壞的通知,他需要聯繫電腦屏幕上的號碼尋求幫助;於是他按照指示撥打後,對方聲稱他為微軟(Microsoft)工作,他告知該男性受害者,其手機和銀行帳戶發現了可疑活動,需要支付1萬6000元現金來解決問題。
該男性受害者照做後,一名不明男子在1月19日上門收走了這筆錢;次日,該受害者接到另一名男子的電話,指示他再取1萬5000元現金,當男子前來收錢時,受害者通知了警方。
經調查,納蘇郡警察局逮捕了來自皇后區的47歲陳榮(Rong Chen,音譯)和來自賽奧塞(Syosset)的46歲余振生(ZhenSheng Yu,音譯)。他們均被提告重竊罪,並已於近日受到審訊。
據悉,近來在紐約周邊地區發生多起類似案件。上月,一名來自長島谷流(Valley Stream)的67歲老人,在發現電腦出現技術問題,撥打一位「技術代表」的電話,並向這位技術代表支付3萬2500元現金以期解決問題,警方隨後逮捕了報住在曼哈頓的43歲黃維序(Weixu Huang,以下均為音譯)和報住在布碌崙(布魯克林)的41歲游永梅(Yongmei You)。當地警方因此敦促社區保持警惕,並提醒易受騙的家庭成員、朋友和鄰居注意可能的詐騙或欺詐行為。
—
83-year-old targeted in Long Island Microsoft scam
Two people allegedly bilked him out of $31,000 before he figured out what was going on, police say
Four people have been arrested in the past two weeks for allegedly pulling off very similar scams on Long Island. It’s not clear if the cases are connected, but one of the victims who lives in Great Neck wants others to be aware that anyone can fall for the ploys. NBC New York’s Pei-Sze Cheng reports.
Authorities arrested two people in connection with a tech scam that targeted an 83-year-old Long Island man, Nassau County police said Tuesday — and some of the claims against the suspects are remarkably similar to other recent incidents.
The alleged crime in question dates back to mid-January but the defendants, 47-year-old Rong Chen of Fresh Meadows and 46-year-old ZhenSheng Yu of Syosset, were arrested Monday. Yu was arraigned Tuesday on grand larceny charges, and pleaded not guilty. Chen was arraigned on the same charges a day before.
The pair is accused of scamming a Great Neck man out of $31,000.
According to detectives, the duo sent a popup notification to the victim’s computer around 1 p.m. on Jan. 18 indicating that the device had been compromised and he should call the provided number on the screen for assistance.
“They were very convincing,” said the victim, who did not wish to be identified. “Something flashing on my computer screen that said ‘your computer is completely locked,’ and a [phone] number flashed on the screen.”
When he called the number, the person who answered the phone claimed to work for Microsoft and told the victim suspicious activity had been detected on his phone and personal bank account. The individual asked the 83-year-old to withdraw $16,000 in cash to rectify the problem. The victim complied, and a man showed up to collect the funds the next day.
The day after that, they bilked him again — this time for $15,000 — with the same ruse.
“They said one was for buying guns and one for gambling,” said the victim. “Both are for federal crimes, so before you know, [the] FBI is going to come and arrest you.”
While the victim did not purchase guns or gamble, he said the speaker was very convincing. To confirm what had been said to him over the phone, the victim called his bank.
“When I called my bank to check on that, apparently they hacked my phone and rerouted to their own personnel. They said those amounts were missing and I had to replace it,” the man said.
Yu was seen on cellphone video at the victim’s house allegedly making a pickup.
Police say the victim was contacted again, but he had wisened up to the scam by the third contact. He refused to comply and called the police, who came to his Nassau County home to make the arrests.
Information on possible attorneys for Yu and Chen wasn’t immediately available.
Those were the most recent arrests in a troubling string of scams. On Saturday, 39-year-old Xiuyu Dong, of Brooklyn, was charged for attempting to scam a Manhasset woman out of $10,000. Prosecutors alleged the victim was contacted by the so-called fraud department of a bank, and that if she did not pay she would be arrested by the FBI and that “snipers” were outside of her house.
In the first week of April, 31-year-old Yongkang Weng, also of Brooklyn, was arrested before he could steal $30,000 from a 67-year-old woman after falsely telling her that she owed that money from a gambling debt.
Police declined to speak to NBC New York regarding the most recent alleged scam, but the victim said this can happen to anyone and he hopes others will learn from his loss.
“The cops should find out who is the mastermind of this thing and go after them,” the victim told News 4.
Anyone with information on the scam — or believes they may have been a victim — is urged to call Nassau County Crime Stoppers at 1-800-244-TIPS.
—
83-year-old Long Island man scammed out of $32K in elaborate computer scam
SADDLE ROCK, Long Island (WABC) — An 83-year-old Saddle Rock man was scammed out of nearly $32,000 as part of an elaborate scheme by two men who claimed to work for Microsoft and told him his computer had been compromised.
Police say the victim got a notification on his computer on Jan. 18 that his device was compromised and he needed to contact the number on the screen for assistance.
The suspect told the victim that he worked for Microsoft and there was suspicious activity on his phone and his personal bank account.
The victim was told he needed to withdraw $16,000 in cash to fix the problem and complied with the request on Jan. 19.
Then, police say, the victim was contacted again for an additional $15,000 in cash and a second man collected the money on Jan. 20.
When the victim was contacted a third time, he refused to comply and contacted police.
After an investigation, authorities arrested 47-year-old Rong Chen and 46-year-old ZhenSheng Yu on Monday. They are both charged with grand larceny.
Nassau County police are urging the community to be alert and to remind vulnerable family members, friends and neighbors about potential scams or fraud.
Anyone with additional information is asked to contact Nassau County Crime Stoppers at 1-800-244-TIPS or call 911. All callers will remain anonymous.
2024.4.4,谷歌起诉加密诈骗者涉嫌将虚假应用程序上传到 Android 应用商店
谷歌周四对一群加密货币诈骗者提起诉讼,指控他们在全球范围内诈骗了超过 10 万人。
谷歌表示,它是同行中第一个对加密货币诈骗者采取行动的公司。
该公司旨在利用诉讼作为制定法律先例的方式来保护其用户。
不再容忍上傳假App至應用商店 谷歌提告加密貨幣詐騙集團
谷歌周四 (4 日) 對一群加密貨幣詐騙者提告,指控他們在 Google Play 上傳欺詐性投資和加密貨幣交易應用程式,欺騙了全球超過 10 萬人。
谷歌表示,它是第一家對加密貨幣詐騙者採取行動的科技公司,這樣做是為了建立法律先例,為用戶提供保護。訴訟指出,被告「為了將其欺詐性應用程式上傳到 Google Play,向谷歌做出多次虛假陳述,包括不限於對其身份、位置以及所上傳應用程式的類型和性質的虛假陳述」。
這家 Alphabet (GOOGL-UD) 旗下的公司正在根據詐騙者影響和腐敗組織 (RICO) 法案提起民事索賠,並對詐騙集團提出違約索賠。該公司表示,該詐騙集團創立並發布至少 87 個欺詐應用程式來欺騙用戶。
谷歌總法律顧問普拉多 (Halimah DeLaine Prado) 接受《CNBC》採訪時表示:「這對我們來說是一個獨特的機會,可以利用我們的資源來實際打擊不良行為者,這些不良行為者正在運行廣泛的加密貨幣計劃來欺騙我們的用戶。」
她說,「光是 2023 年,美國就有超過 10 億美元的加密貨幣詐欺和騙局,這次訴訟不僅能夠利用我們的資源來保護用戶,而且還為我們未來的不良行為者提供了先例。不能容忍這種行為。」
該訴訟在紐約南區提出,被告分別為 Yunfeng Sun (又名 Alphonse Sun) 和 Hongnam Cheung (又名張洪寧,Zhang Hongnim) 或費雪 (Stanford Fischer),至少從 2019 年起就開始詐騙。訴訟指出,兩名被告透過三種方法誘騙受害者從 Google Play 和其他來源下載應用程式,使用 Google Voice 向主要在美國和加拿大的受害者發送簡訊,並在 YouTube 和其他平台上傳宣傳影片以及支付用戶佣金的聯盟行銷活動用於註冊人員。
訴訟稱,Sun、張及其代理人將這些應用程式設計得看來合法,向用戶說明他們正在維持應用程式上的餘額並賺取投資回報。然而,用戶無法撤回他們的投資或聲稱的收益。
訴訟指出,為了讓用戶相信這些應用程式是值得信賴的,被告允許用戶最初提取少量資金。據了解,其他人被告知需要支付費用或達到最低餘額才能提取資金。谷歌說這種策略「騙走一些受害者更多的錢」。
—
Google sues crypto scammers for allegedly uploading fake apps to Android app store
•Google filed a lawsuit on Thursday against a group of crypto scammers, alleging they defrauded more than 100,000 people globally.
•Google says it’s the first among its peers to take action against crypto scammers.
•The company aims to use the litigation as a way to set legal precedents to protect its users.
Google filed a lawsuit on Thursday against a group of crypto scammers, alleging they defrauded more than 100,000 people across the globe by uploading fraudulent investment and crypto exchange apps to Google Play.
Google says it’s the first tech company to take action against crypto scammers, and is doing so as a way to set a legal precedent to establish protections for users. The lawsuit claims the defendants made “multiple misrepresentations to Google in order to upload their fraudulent apps to Google Play, including but not limited to misrepresentations about their identity, location, and the type and nature of the application being uploaded.”
The Alphabet-owned company is bringing civil claims under the Racketeer Influenced and Corrupt Organizations (RICO) law as well as breach of contract claims against the group of scammers, who the company said created and published at least 87 fraudulent apps to dupe users.
“This is a unique opportunity for us to use our resources to actually combat bad actors who were running an extensive crypto scheme to defraud some of our users,” Halimah DeLaine Prado, general counsel at Google, told CNBC Crypto World in an exclusive on-camera interview.
“In 2023 alone we saw over a billion dollars within the U.S. of cryptocurrency fraud and scams and this [lawsuit] allows us to not only use our resources to protect users, but to also serve as sort of a precedent to future bad actors that we don’t tolerate this behavior,” she added.
The lawsuit, filed in the Southern District of New York, said the alleged scammers, identified as Yunfeng Sun, also known as Alphonse Sun, and Hongnam Cheung, also known as Zhang Hongnim or Stanford Fischer, conducted their scheme since at least 2019. The two allegedly lured victims to download their apps from Google Play and other sources through three methods: text message campaigns using Google Voice to victims primarily in the U.S. and Canada, online promotional videos on YouTube and other platforms, and affiliate marketing campaigns that paid user commissions for signing up people.
Sun, Cheung and their agents designed the apps to appear legitimate, showing users that they were maintaining balances on the app and earning returns on their investments, the lawsuit said. However, users couldn’t withdraw their investments or purported gains.
In an effort to convince users that the apps were trustworthy, the defendants would allow users to initially withdraw small amounts of money, according to the suit. Others were allegedly told they needed to pay a fee or have a minimum balance to withdraw their money, ploys that Google said “bilked some victims out of even more money.”
“Unfortunately, as new technology arises, bad actors exploit that technology to try to defraud users,” DeLaine Prado said. “We have teams that work around the clock to detect fraud and spam and abuse and when we find a unique instance in which we can actually go a step further, we’ll actually engage in affirmative litigation filing a lawsuit to actually create legal protections for our users in a more constructive way.”
One app highlighted in the suit was TionRT, which claimed to be a crypto exchange. Google said the app was uploaded to Play in 2022 by a developer account associated with Sun. Members of the alleged fraud scheme used text messages and social media platforms to lure victims into downloading the app and using it for investing, with the promise of earning extra money, according to the complaint.
TionRT appeared legitimate because of news releases about the app published on newswire service websites, the suit said. When victims complained to the texters that they were later unable to withdraw their money, they wouldn’t get responses, according to Google. The platform was eventually shut down.
Google was alerted to the fake apps by victims, who contacted the company after unsuccessful efforts to withdraw their funds.
“We have a dedicated cybersecurity team that is constantly looking across all of our platforms and services to look for opportunities where we can do more or where we think that users are being abused,” DeLaine Prado said. In some cases, Google partners with law enforcement, she added.
Google said in the complaint that when it would take the apps offline, the scammers would create new ones and upload them to Google Play, using “varying computer network infrastructure and accounts to obfuscate their identities, and making material misrepresentations to Google in the process.”
Google claims it suffered damages in excess of $75,000 by incurring expenses to investigate the breach and on safety and integrity resources. The company is seeking a permanent injunction against the defendants for general damages and to prevent them and their employees from creating Google accounts and accessing Google services.
—
Google sues alleged scammers over fake crypto investment apps
•Two Chinese nationals allegedly promoted fake crypto investment apps
•Defendants took thousands of dollars from Google users, lawsuit says
April 4 (Reuters) – Google (GOOGL.O), opens new tab sued two Chinese nationals in New York federal court on Thursday, accusing them of misusing its Google Play app store to scam thousands of users out of their money through dozens of fake cryptocurrency investment applications.
The lawsuit said, opens new tab that Yunfeng Sun in Shenzhen and Hongnam Cheung in Hong Kong were involved in a scheme to lure users into giving them money via the fake platforms, leading to up to tens of thousands of dollars in losses per victim since 2019.
Google accused Sun and Cheung of racketeering and violating the company’s terms of service and other policies. Sun and Cheung could not immediately be reached for comment on the lawsuit.
“Keeping people safe online is core to our business and we will not tolerate the misuse of our platforms to facilitate cryptocurrency scams,” Google general counsel Halimah DeLaine Prado said in a statement. “This litigation is a critical step in holding these bad actors accountable.”
Google said that Sun and Cheung engaged in a “social engineering” scheme to lure victims to their apps through “wayward” text messages.
“The texts would purport to be from wrong numbers, but then the texters would strike up conversations with the victims, developing ‘friendships’ and ‘romantic attachments,’” the complaint said.
The alleged fraudsters would then convince victims to “invest” through the apps and allow them to withdraw only small amounts of their “returns,” according to Google.
“When users tried to withdraw larger amounts of their ‘earnings,’ they were told to pay more money,” Google said. “When victims complained to the ‘friend’ or ‘romantic partner’ who had so helpfully guided them through the process, the ‘friend’ or ‘romantic partner’ would simply disappear.”
The lawsuit also said that Sun and Cheung used YouTube videos, social media ads and fake press releases to make the apps seem more legitimate.
Google said that it has disabled 87 fake apps from Sun and Cheung over the past four years that have been downloaded by nearly 100,000 users worldwide.
The case is Google LLC v. Sun, U.S. District Court for the Southern District of New York, No. 1:24-cv-02559.
For Google: Timothy Howard of Freshfields Bruckhaus Deringer US
For Sun and Cheung: attorney information not yet available
—
The lawsuit file: GOOGLE CRYPTO SCAMMER LAWSUIT complaint.pdf
2024.4.3,金山金光黨詐騙2華婦 首名嫌犯落網 還有3嫌在逃 部分贓物已分贓
舊金山(三藩市)警方較早前在南加州洛杉磯拘捕一名男子,懷疑他與兩宗舊金山的祈福騙局有關。
舊金山警方週三公佈,在調查兩宗舊金山發生的祈福騙局後,探員在2月26日在南加州洛杉磯拘捕一名懷疑涉案男子,68歲的Chen Kun Lo,並發現疑犯除了持有相信是從祈福騙局受害者偷來的物品外,還持有兒童色情物品。
警方表示,兩宗祈福騙案分別發生在1月23和25日,1月23日早上約11時30分,一名女受害人在Excelsior區獨自等巴士時,突然有一名陌生男子和受害人搭訕,過程中再有兩名女子加入對話,對話內容圍繞著妖魔鬼怪。
幾名騙徒說服受害人將家中貴重物品交給他們祈福,受害人交出的現金及珠寶,最終不翼而飛。
第二宗騙局就發生在25日下午近4時,手法也差不多,受害人獨自在Outer Mission區行走時,突然有一男、一女和受害人搭訕,之後有一名女子加入對話。
幾名騙徒說服受害人將家中貴重物品交出來,給他們進行祈福儀式,後來受害人發現,她的貴重物品被換成類似重量的物品。
警方表示,案中其他疑犯仍然在逃。
金山金光黨詐騙2華婦 首名嫌犯落網 還有3嫌在逃 部分贓物已分贓

舊金山警局3日表示,涉詐騙兩位金山華裔老年女性的「金光黨」一名華裔嫌犯盧辰昆(音譯,Chen Kun Lo)在洛杉磯被逮捕。他因藏有兒童色情物品、持有贓物的重罪指控而被收監。這意味著,最近兩起詐騙案的首個嫌犯落網。
警長史考特(Bill Scoot)曾指出,這兩位受害者損失的珠寶和現金價值數十萬(hundred of thousands)。警方知情者表示,因疫情等原因,這是時隔五年後,金山首次出現金光黨騙局。
這類騙局一般由歹徒佯稱可為受害人祈福,再從中騙取、掉包財物,也被稱為「祈福黨」。
兩起案件中,有四個嫌犯,為一男三女,被抓獲的男性嫌犯是開車司機,其他人還在逃。截獲的車輛中,只有部分受害者被騙的珠寶首飾,其他都已被分贓。據知情人士表示,其實金山近期共有五起金光黨騙局,受害者損失30多萬。「提醒公眾,不要理會陌生人攀談、不要跟著走入小巷、別相信什麼祈福驅除邪靈,避免落入圈套。」
前述兩起騙局的受害者,都是舊金山的華裔老年女性。1月23日上午11時30分,在 Excelsior區一名受害者正獨自在等公車。一名身分不明男子走近與受害人交談。過程中,兩名陌生女性加入,並幫助說服受害人從家中取出貴重的物品進行祈福。受害人稱,祈福儀式後,發現貴重物品不翼而飛。
另一起詐騙案發生於1月25日下午4時許,當時受害人獨自在米慎區(Mission)散步,有不明身分的一男一女人走了過來並與受害人交談。之後,雙方走進了一條小巷,這時又有另一名陌生女性加入交談。受害人被說服取來她的美元和珠寶祈福,犯罪嫌疑人在儀式上對貴重物品進行了加持。受害人後來發現,財物被掉包成重量相似的物品。
金山警局特別受害者小組領導案件的調查工作。調查人員找到犯罪所用的車輛,並確定嫌疑人的身分。在搜查車輛的過程中,發現並繳獲與這兩起祈福詐騙案有關的證據。調查人員向其中一名嫌疑人發出逮捕令。2月26日,在洛杉磯地區找到68歲的男性嫌犯盧辰昆,並順利將其逮捕。
調查人員發現,盧辰昆藏有據信是從祝福詐騙案受害者處偷竊的物品,以及藏有兒童色情物品。盧因持有贓物和兒童色情製品的重罪指控而被收監。調查人員已確認了其他嫌疑人的身份,他們目前仍然在逃。
警方表示,雖然已逮捕一人,但調查仍在進行中。任何知情者可致電金山市警察局舉報專線,1-415-575-4444或發送短信至TIP411,並在短信開頭註明舊金山警局。舉報者可以保持匿名。
—
SF ‘blessing scam’ suspect caught with child pornography while being arrested
SAN FRANCISCO – A man accused of multiple blessing scams in San Francisco has been arrested and charged for the scams, but also for being in possession of child pornography, according to the San Francisco Police Department.
Police arrested Chen Kun Lo in the Los Angeles area on Feb. 26. He was found to have some stolen items, but also child pornography.
One blessing scam incident occurred on Jan. 23 around 11:30 a.m. when a victim was waiting at a bus stop in the Excelsior District. There, the 68-year-old allegedly approached a victim, striking up a conversation when two other women joined them and helped convince the victim to get her “most valuable items” from her home to be blessed.
A ceremony “blessing” the items was done, in which the victim’s items disappeared.
A second incident two days later around 4 p.m. occurred in the Outer Mission neighborhood when an unknown man and woman approached a victim. The two suspects struck up a conversation with the victim and walked down an alley where a second woman joined the trio.
The suspects convinced the victim to participate in the blessing with their jewelry and money. It wasn’t until later did the victim realized their items were switched with similar weighted items.
SFPD’s Special Victims Unit investigated the crimes and found a car linked to both incidents. Upon seizure of the suspected car, evidence linking to both crimes was found.
Lo was arrested without incident and allegedly found to be with stolen property belonging to the blessing scam victims and child pornography. He was booked on felony charges in the San Francisco County jail on March 9 for these allegations.
He’s due to appear in court on April 9.
The other suspects have not been publicly identified.
Anyone with information about the blessing scams is asked to contact SFPD at (415) 575-444 or text a tip to TIP411 beginning with SFPD. Cantonese-speaking victims can leave tips at (415) 553-9212.
—
Chen Kun Lo Arrested For Blessing Scam By SFPD
SAN FRANCISCO—On Wednesday, April 3, the San Francisco Police Department announced in a news release that a suspect involved in a Blessing Scam was arrested.
The SFPD reported on January 23, at approximately 11:30 a.m. a blessing scam transpired where a victim was waiting by herself for the bus in the Excelsior District. The victim was approached by an unknown male who started a conversation with the victim. During the conversation, two unknown females joined and helped convince the victim to retrieve her most valuable items from her home to be blessed. After the victim gathered the items, a ceremony was conducted with the victim’s valuables. The victim later discovered her valuables were gone.
On January 25, at approximately 4 p.m. another blessing scam transpired where a victim who was walking by herself in the outer Mission was approached by an unknown male and female. The two subjects started a conversation with the victim.
As the conversation continued all parties walked into an alley where a second unknown female joined them. The suspects convinced the victim to gather her valuables to be blessed. The victim gathered US Currency and jewelry which was blessed by the suspects in a ceremony with the victim’s valuables. The victim later discovered her valuables were switched with similar weighted items.
The SFPD Special Victims Unit (SVU) has been leading the investigations. SVU investigators were able to locate the vehicle used in the crimes and identify the suspects. Investigators developed probable cause to obtain a search warrant for the suspect vehicle, which was located and seized. During the search of the vehicle, evidence was located and seized that was linked to both blessing scams.
Investigators developed probable cause to obtain an arrest warrant for one of the suspects. On February 26, SVU investigators located the suspect, Chen Kun Lo, 68, in the Los Angeles area and arrested him without incident.
During the arrest, investigators found Lo in possession of items believed to be stolen from the blessing scam victims, as well as possession of child pornography. He was booked for the felony charges of possession of stolen property (496(a) PC) and possession of child pornography (311.11(a) PC).
Investigators have identified the other suspects who are still at large at present. Anyone with details is asked to call the SFPD Tip Line at 1-415-575-4444 or Text a Tip to TIP411 and begin the text message with SFPD.
2024.3.27,加州洛杉矶县23岁的华人高志(Zhi Gao,音译)因参与诈骗圣地亚哥居民,近日被圣地亚哥法官判罪。
参与诈骗圣地亚哥老人 洛杉矶华人青年被判
按照之前达成的认罪协议,法官判处高志2年缓刑,包括期间不得购买枪支等限制。
高志在今年2月底对“窃盗未遂”罪认罪,加上他已经向受害者偿还了之前骗取的3万美元,使他免于入狱。但是法官说,这仍然是一个重罪纪录。
高志于2023年10月12日被捕,当时他从洛杉矶的圣盖博(San Gabriel)到圣地亚哥受害者家,计划再次骗取3万美元的现金,但是被警察当场逮捕。
检察官说,受害者是住在圣地亚哥的一名65岁、患有疾病的妇女。高志是中国国籍,持有美国签证,他参与了这场让该妇女被骗走超过20万美元毕生积蓄的诈骗。
在去年圣地亚哥县地方检察官对高志提起诉讼时,检察官素默•史蒂芬(Summer Stephan)说,骗子先是通过电脑对该妇女进行诈骗,让她的电脑上出现一条貌似来自微软的讯息,她拨打了弹出视窗中显示的电话号码,寻求帮助,以解除她电脑被冻结的状态。最终她支付了骗子120美元来“修理”她的电脑。
骗子得手后将骗局扩大。这次骗子说自己与大通银行(Chase Bank)有关联,并说银行已收到警报,有诈骗者入侵了该妇女的账户。为了保护她的钱,她必须从她的账户中提取资金,并将其交给银行,以便在反诈欺部门为她调查此案时,这些钱可以被存放在一个安全的账户中。
地方检察官办公室说,受害者多次提款,每次提款金额从2万美元到3万美元不等,并将现金交给出现在她家门口的收款人。
检察官办公室说,这是一个跨国诈骗集团的行动,高志是其中一个收款人。
该妇女的家人在定期的对账户的检查中发现了这些可疑活动,并联系了警方。因此当高志后来再次出现在该妇女门前,准备再拿走3万美元现金时,警察也出现了,并逮捕了他。
检察官斯蒂芬表示,该案中采用的诈骗是针对老年人最常见的诈骗,并表示这“强烈提醒老年人及其家人注意诈骗的警告信号并寻求帮助”。
—
Man sentenced to two years probation for scamming elder out of thousands of her life savings
SAN DIEGO — A man accused of scamming a San Diego woman out of thousands of her life savings learned he will not go to prison. During his sentencing, Zhi Gao was ordered to two years of felony probation for attempted burglary.
The sentence comes from a plea agreement when Gao pleaded guilty to attempted burglary and paid back the amount stolen from the victim.
However, the deputy district attorney said Gao is just a piece of this prevalent scam that has taken millions of dollars from thousands of San Diegans.
“You will be granted felony probation through the court, it remains a felony,” said a San Diego County Superior Court Judge.
Prosecutors said Gao was a courier in a theft ring that defrauded a 65-year-old San Diego woman out of thousands of dollars.
Prosecutors said it started last October when the woman’s computer froze and then a message appearing to be from Microsoft popped up with a number to call.
“The scammers quickly convince our victims that because their computers have been hacked that their financial accounts are also at risk,” said Scott Pirrello, San Diego County Deputy District Attorney.
The woman called the popup number and got charged $120 to fix the problem, but prosecutors said the scammers were not done.
Pirrello said suspects from around the world would instruct the woman to hand over money or gold to a courier while they “investigate” the bank fraud.
“And what they are asking our victims to do is to transfer money out of their bank accounts into another account that they link is to save their money. They think they’re working with government or their bank to actually save their money from the hackers,” Pirrello said. “A scammer might ask them to wire a certain amount, they might come to pick up cash, they might ask our victims to send cryptocurrency.”
The woman eventually gave more than $200,000 from her life savings to various scammers.
Pirrello said this included when Gao drove from Los Angeles to San Diego to collect $30,000 from the women. However, the woman’s family had already reported the suspicion to the police, who with the FBI and DA’s office set up a sting operation.
“He was arrested by our task force who was waiting for him at the victim’s house,” Pirrello said.
Gao’s guilty plea of attempted burglary, plus reimbursing the victim her $30,000 allowed him to avoid a prison sentence.
“For our victims, every pen counts that we can get back because sadly, for 99.9% of our victims when they fall victims to these, it’s too late we can’t get their money back. So it is a real success that we were able to get this family just $30,000 back,” Pirrello said.
Gao must follow the rules of his probation including not owning a firearm, or he will go to prison to serve his full sentence of a year and six months.
—
Man Who Helped Scam 65-Year-Old Woman Out of Life Savings Gets Probation
A man who took part in scamming a 65-year-old San Diego woman out of more than $200,000 of her life savings was sentenced Wednesday to two years of probation.
Zhi Gao, 22, was arrested last fall when he arrived at the woman’s door to pick up a package of cash, one of several she had handed over to scammers, prosecutors said.
Gao pleaded guilty last month to an attempted burglary count, which included an agreement to probation and a time-served sentence if he agreed to pay $30,000 in restitution to the victim, which has been paid.
Prosecutors said the woman was manipulated by scammers to make major cash withdrawals from her bank and hand her money to Gao and his co- conspirators over the course of several weeks.
During a news conference held last fall to announce the charges against Gao, San Diego County District Attorney Summer Stephan said the scam began with a pop-up message that appeared on the woman’s computer. Believing that the message originated from Microsoft, she called a phone number displayed on the pop-up to receive help with her computer, which was frozen. The woman paid scammers $120 to fix her computer.
The scam later moved to a banking-related fraud, in which scammers pretended to be associated with Chase Bank. This time, they alleged that the bank had been alerted to fraud on her account. In order to protect her money, she would have to withdraw it from her account and hand it over to the co- conspirators “so that the money could be secured in a safe account while the fraud division investigated the case for her,” Stephan said.
The victim made multiple withdrawals ranging from $20,000 to $30,000 each time, the DA’s Office said, and gave the cash to couriers who showed up on her doorstep.
Her family eventually caught wind of the suspicious financial activity and contacted police.
Gao was arrested during a sting operation in which he was due to pick up another $30,000 from the victim, prosecutors said.
Stephen said the scams employed in the case were among the most common perpetrated against seniors and said it served as “a compelling reminder to seniors and their families to be aware of the warning signs of a scam and reach out for help.”
2024.3.25,康科德警方与 HSI 破获数百万美元礼品卡诈骗案
经过数月的调查后,两名纽约人和一名纳舒厄(Nashua)男子被捕;警察、联邦调查局查获了价值数百万美元的电子设备。
新罕布夏州康科德警方近期捕獲三名涉嫌盜竊詐欺禮品卡的華人嫌犯
新罕布夏州康科德(Concord)警方近期逮捕三名涉嫌盜竊禮品卡的華裔,其中兩人來自紐約市,他們盜竊未使用的禮品卡後記錄卡號等信息,再恢復原狀放回商店,等到顧客購買卡片充值後,嫌犯利用卡片額度購買昂貴電子產品,再轉手賣出;警方表示,背後可能有一亞裔犯罪團夥,涉及數百萬元禮品卡詐騙。
根據康科德警方,該團夥偷竊數百甚至數千張未激活的禮品卡,記錄卡號、PIN碼和其他信息,重新包裝或恢復禮品卡原狀,將它們放回商店並重新擺放到貨架上。當顧客購買並在結帳時為禮品卡充值後,全天候監控所有禮品卡號的團夥,就會立刻發現卡內添加了餘額,並將所有卡片信息轉給另一組嫌犯,用來購買電子產品或其他昂貴物品,如蘋果平板、手機和電腦,再由第三組嫌犯轉手銷售,他們在單次交易中,曾使用12張或更多禮品卡。
根據報告,目標百貨(Target)和沃爾瑪(Walmart)禮品卡是該團夥的主要目標,受害人遍及全美;且該犯罪團夥主要由亞裔組成,他們通常不相識,通過聊天軟件溝通,居住地多為加州和紐約州。
自去年假日季節以來,康科德警方發現這類犯罪活動明顯增多,因而開始進行調查。2023年12月28日,警方收到一名來自阿拉巴馬州的男子報告,他表示剛買的禮品卡在康科德的沃爾瑪被使用,但使用者不是他。警方隨後與商店員工合作,追蹤到一輛帶有紐約車牌的賓士轎車。
沃爾瑪從檔案中,發現此人叫陳明東(MingDong Chen,以下姓名均為音譯),警方根據車牌資料,確定陳明東28歲、居住在紐約市,並於隔日在同一沃爾瑪停車場將其逮捕。
陳明東透過翻譯對警方表示,他八年前來美,到新罕布夏州共五次,因為該州沒有銷售稅(Sales Tax),主要任務是用禮品卡為他的「上線」購買蘋果的平板和其他產品;他再將物品帶回紐約、運往中國,每買一台設備可獲得10元報酬。他僅透過微信與「上線」溝通,不清楚對方身分。
在調查陳明東時,警方發現他手機上指向該州納施華(Nashua)某公寓的訊息,並前往調查,發現大量蘋果電子設備、現金以及一個似乎正在實時運行禮品卡號碼的電腦程序。
25歲報住在紐約市的華女吳納新(Naxin Wu)就住在公寓內,警方在臥室查獲24部藏於梳妝台的蘋果手機、衣櫃中的50部蘋果手機、一部谷歌手機,以及帳本和2萬7750元現金。後來根據監控錄像,警方還發現吳納新在新罕布夏州多家沃爾瑪進行欺詐性購買。
公寓內運行禮品卡號程序的電腦,則屬於33歲華人蔣夢影(Mengying Jiang),報住在納施華。在警方搜查公寓期間,國際快遞優比速(UPS)正好上門送達15個快遞,幾乎都是蘋果手機,該快遞員說,他們每天要送四次包裹給這間公寓,大都是蘋果產品。
目前,陳明東和蔣夢影均被控以組織零售犯罪企業罪(organized retail crime enterprise)和欺詐盜竊銷贓罪(theft by deception with intent to redistribute stolen goods),已被關押在當地監獄;吳納新則被控欺詐轉售分銷重罪(theft by deception resale distribution),若罪名成立,最高刑期可達20年。三人保釋金均為50萬元,將在4月和5月於當地出庭。
—
Concord Police, HSI Bust Multi-Million Dollar Gift Card Scam Operation
2 New Yorkers and a Nashua man arrested after a multi-month investigation; cops, feds seize millions of dollars worth of electronic devices.
Posted Mon, Mar 25, 2024 at 6:58 pm ET | Updated Tue, Mar 26, 2024 at 10:25 am ET




CONCORD, NH — Concord police officers and detectives have arrested three theft suspects who may be part of a multi-million-dollar gift card scam crime ring, according to police.
Beginning during the holiday season last year, Concord police were made aware of a “complex system of scammers” who worked together, using technology, to scam stores and outlets of funds. The scam involves stealing hundreds or even thousands of inactivated gift cards, recording the card number, PIN number, and other information, repacking or restoring the gift cards, returning them to the store, and placing them back on the shelves. A customer then goes to the store, selects a card, adds the funds at checkout, and leaves. The criminals then constantly monitor all the gift card numbers. Once the balance is added to a card, the information is given “to a different group of suspects,” who purchase electronics or other expensive items. The electronics and other items like Apple iPads, iPhones, and computers were purchased by another group of suspects and then resold.
The suspects who purchased the electronics were paid a small sum per item. Target and Walmart were two of the primary targets of the thieves, with the suspects using as many as a dozen or more cards in a single transaction, the report stated. However, the detective wrote unsuspecting victims purchased the cards nationwide.
“Many of the gift card numbers used by the suspects were already reported lost or stolen to police departments or Walmart,” the detective said.
The criminals, “mainly perpetrated by individuals of Asian descent,” according to investigators, often do not know each other but communicate, instead, through mobile applications, a detective wrote in several affidavits. They reside in California and New York. According to police, there was an uptick in these crimes in Concord during the 2023 holiday shopping season.
“Since the onset of this investigation,” the detective wrote, “millions of dollars worth of electronic devices have been seized by the Concord Police Department and HSI at various storage and shipping locations in New Hampshire operated by the involved suspects.”
An Arrest In December 2023
On Dec. 28, 2023, police received a report from a Hoover, Alabama, man who told police a gift card he purchased in that state had been used at the Concord Walmart store, but it was not him.
Detectives worked with the loss prevention employee at the store to track down a suspect vehicle — a Mercedes sedan with a New York plate. The man was described as a younger-looking Asian man, an affidavit stated. The loss prevention employee said the suspect was involved in “several other thefts” at the store using stolen cards and purchasing high-end electronics, a report stated.
Walmart had the name of MingDong Chen in its files and a detective ran the registration and found the car belonged to MingDong Chen, 28, of 8th Avenue in Brooklyn, New York, an affidavit said. The surveillance video at the store also matched his driver’s license photo, the detective wrote.
Officers were given an intelligence briefing about the case to be on the lookout for the vehicle or the suspect. The next day, an officer on foot patrol in the parking lot of Walmart spotted the vehicle and said the suspect was driving the vehicle, according to a report. Officers stopped the vehicle and the detective headed to the store while also informing the officers to ensure Chen was not able to alter his cellphone in any way, the report said.
“I was concerned that evidence could be altered or destroyed if he was able to manipulate the phone,” the detective wrote.
When the detective arrived, he checked Chen’s license to confirm it was him and saw iPads in a Target bag in the back seat of the vehicle, the report stated. The affidavit said Chen’s cell and vehicle were seized while a search warrant could be requested.
The detective accused Chen of agreeing to come to headquarters to speak to him about the case, and a Mandarin phone interpreter was lined up for the interview. Chen, who moved from China about eight years ago, said he came to the state about five times and had purchased iPads with gift cards for his boss, the report said. He slept in his car when he was here, the detective wrote. When asked about his boss, Chen said he did not know and only communicated with him via WeChat, the affidavit said.
Chen was accused of confirming this was his only job and purchased iPads, ear pods, Apple Watches, and printer ink — noting it was cheaper to drive up to New Hampshire to purchase the items due to the state having no sales tax. The merchandise, he said, was brought back to New York and then shipped to China. He received $10 per device, the report said.
When asked where his drop-off was in New York, Chen was accused of saying he did not know off the top of his head, but it was on his cell phone. During his current trip to New Hampshire, he purchased items with the cards from Concord, Hooksett, and Salem, the report stated.
The day before, according to the report, he purchased four iPads at Walmart, which “were conducted using several Walmart gift cards” the report.
Chen was arrested on organized retail crime enterprise and theft by deception with intent to redistribute stolen goods, both felonies. He refused bail and was sent to the county jail.
Two Arrested In March
Two more suspects were arrested in March after incidents at Walmart.
Naxin Wu, 25, with a last known address of 47th Street in Brooklyn, NY, was arrested at 1:45 p.m. on March 5 on a felony theft by deception resale distribution charge. Mengying Jiang, 33, of Harbor Avenue in Nashua was arrested about two hours later, at 1:53 p.m. on March 5, on organized retail crime enterprise and theft by deception with intent to redistribute stolen goods, both felonies.
While investigating the Chen case, detectives found “documentation” on his cell phone that led to an apartment in Nashua.
A search warrant was requested and granted. On Jan. 4, “a large quantity of Apple brand devices, cash, and a computer program that appeared to be running gift card numbers, in real-time,” according to an affidavit.
Wu, the affidavit said, was one of the occupants of the apartment — with the master bedroom “containing almost exclusively female items.” Jiang was also at the apartment during the search.
Police seized 24 Apple iPhones, hidden in the master bedroom bathroom vanity, 35 iPhones in a master bedroom closet, 15 iPhone Pro Max devices, a Google phone, $4,000 in cash, ledgers, and $23,750 in cash.
“While executing the search warrant,” the detective wrote, “a package delivery drive from UPS arrived at the apartment with a delivery of 15 packages.”
The packages contained iPhones. The UPS driver said they made approximately four daily deliveries to the apartment, primarily Apple products.
Detectives said they found several ledgers written in Chinese, but some information was readable, including names and store transaction amounts next to each name. The ledgers, the reporting detective wrote, “appeared to be extensive and did not appear on their face to be related to personal retail transactions.”
A laptop Jiang said was his had a screen open and appeared to be running some sort of software involving a large number of gift card numbers, the detective said.
Detectives began working with an investigator from Walmart Global Investigations, who was given gift card numbers found on Wu’s phone, a report stated. Screenshots were also taken from her WeChat app on her phone.
One, the report said, read “Kenny-WM BB,” with the investigator believing WM stood for Walmart while BB meant Best Buy. In the message were gift card numbers, PIN codes, and the value of each card, the detective wrote. Most of the cards were also annotated with “New.”
The detective said, sometimes, the cards were declined for various reasons. Wu and Chen, the report said, were in the group of WeChat screenshots.
A spreadsheet created by the Walmart investigator found 13 gift card numbers were used on Dec. 13, 2023. In those transactions, two iPads and a Quest 3 128G device were purchased for $997.
On Nov. 28, 2023, a card that only had $25 loaded on it was used and listed by Walmart as lost or stolen, the report stated.
Another card was activated with $500 at a Walmart in Spokane, Washington, but was used Dec. 13, 2023, in Concord and frozen later by Walmart. The large amount loaded on this card struck the detective as odd, but checked surveillance footage and found it was an older white woman with gray hair, talking on a cell phone and carrying a purse, when she made the purchase. The woman paid for the card with five $100 bills, the report stated.
The detective noted the woman remained unidentified by investigators but may have been the victim of a phone scam. The woman also purchased eight other gift cards, totaling $4,000, during four transactions across five minutes, the report stated.
The detective accused Chen of using one of the cards the woman purchased 24 hours later.
During the investigation, the report said, three more cards were connected to Wu — two $500 cards purchased by a woman from Vancouver, WA, and a third one purchased in Murphysboro, Illinois.
Police interviewed the Vancouver woman who said a person with an accent instructed her to purchase several cards. When she began to doubt the legitimacy later and challenged the person, they became aggressive.
Wu, in a group chat, wrote in Chinese that one of the cards was “stolen,” the detective wrote.
A warrant was then issued for her arrest.
On Jan. 6, the Walmart loss prevention employee located another transaction from Dec. 2, 2023, involving Air Pod Max headphones and an Apple iPad, valued at $748, which were purchased with nine gift cards. One of the cards was from Baton Rouge, Louisiana, the report said.
The detective reviewed the surveillance footage and matched it to Jiang as well as a white Lexus IS300 with New York plates, the report said.
The loss prevention employee said Jiang was also suspected in making fraudulent purchases at numerous Walmarts throughout New Hampshire, an affidavit said.
“These incidents are still under investigation,” the detective said.
A warrant was issued for Jiang’s arrest.
All three arrests were initially booked in Concord District Court but were bound over to Merrimack County Superior Court.
Chen, Wu, and Jiang were held on $500,000 cash bail.
Chen is due in superior court on April 11 for arraignment and a dispositional conference hearing, while Jiang and Wu are due in superior court for a dispositional conference hearing on May 14.
2024.3.26,洛城3華男誘購禮卡詐財超過250萬元 重判8年、10年、15年刑期
洛杉磯縣三名華裔男子與中國詐騙團夥「神燈」(Magic Lamp)合謀,冒充執法人員詐騙當地民眾購買禮品卡,並通過微信售賣、購買電子產品等方式洗錢,涉案金額超過250萬。3名嫌犯日前分別被判8年、10年、15年等刑罰。
3名罪犯分別是35歲的艾爾蒙地市(El Monte)居民白布雷德(Blade Bai,音譯),他犯有兩項共謀洗錢罪,判刑15年,勒令賠償9萬7815元;28歲的哈岡(Hacienda Heights)居民胡博文(Bowen Hu,音譯),判刑10年,賠償5萬7156元;29歲的鑽石吧 (Diamond Bar)居民石泰然(Tairan Shi,音譯),判刑8年,賠償3萬9416元。
據檢察官辦公室稱,經過為期10天的審判,三人均被判欺騙受害者購買禮品卡的罪名。自2019年6月至2020年11月期間,嫌犯共計詐騙、洗錢金額超過250萬元,他們參與複雜的跨國欺詐活動,主要針對長者,騙取他們的積蓄。
當局稱,案件涉及一個名為「神燈」的中國詐騙團夥,嫌犯在電話中冒充執法人員或政府僱員,告訴受害者身分被盜或已發出逮捕令;團夥其他成員則發送詐騙電子郵件,稱受害者的銀行帳戶出錯。為解決這些子虛烏有的問題,受害者被要求購買多張Target禮品卡付款,通常每張金額500元,並向對方提供卡號、密碼。
法庭文件稱,「神燈」詐騙團夥遠程操控,通過微信方式向白布雷德、胡博文、石泰然出售5000多張詐欺所得的禮品卡。三人則利用微信向「車手」(runners)分發禮品卡,後者很快就在洛杉磯縣、橙縣等Target商店購買各種物品,包括昂貴的電子產品等。其中一名「車手」嚴富 (Yan Fu,音譯),60 歲,奇諾岡(Chino Hills)居民,他承認一項共謀洗錢罪名,目前正在監獄服刑20個月,並被勒令賠償4萬8073元。
當局提醒民眾,禮品卡是送給朋友、親人的禮物,不能用於向政府部門或企業付款,不要被聲稱是政府、銀行或其他任何機構的來電者欺騙,要求購買禮品卡;禮品卡不可能解決銀行帳戶、社會安全號、或所謂的刑事案件等問題。任何60歲或以上且經歷過財務詐欺的人,都可以撥打長者詐欺熱線電話1-833-372-8311,尋求幫助;若要舉報禮品卡詐騙,請聯絡聯邦調查局的網路犯罪投訴中心或聯邦貿易委員會,民眾也可以致電 877-382-4357 或當地警察局。
(媒体报道)
3 L.A. County residents sentenced for stealing over $2.5 million in Target gift cards
Three L.A. County residents were sentenced to prison for laundering over $2.5 million in Target gift cards.
The trio was identified as:
•Blade Bai, 35, of El Monte
•Bowen Hu, 28, of Hacienda Heights
•Tairan Shi, 29, of Diamond Bar
After a 10-day trial in September 2023, all three were found guilty of scamming victims into buying gift cards under the false pretense of resolving various financial problems, according to the U.S. Attorney’s Office.
Between June 2019 and November 2020, prosecutors estimate over $2.5 million worth of gift cards were laundered.
The scheme involved a network of scammers calling victims and persuading them to buy one or more Target gift cards to rectify nonexistent issues. The targeted victims were often older adults, officials said.
During these calls, the suspects posed as law enforcement officers or government employees while telling the victims their identities had been stolen or warrants were issued for their arrest. Others were sent fake tech support emails claiming issues with the victims’ financial accounts.
They also posed as retail and tech support staff claiming issues with the victims’ accounts and falsely offering to fix the nonexistent issues.
To resolve these problems, the victims were asked to send payment in the form of Target gift cards, authorities said.
Victims were told to purchase the gift cards, often more than one and typically in increments of $500. They were told to read the card numbers and access codes over the phone to the fraudsters.
Using this method, a China-based scam group known as the “Magic Lamp” sold over 5,000 fraudulent gift cards to the trio through the messaging app, WeChat, court documents said.
The trio used WeChat to coordinate the distribution of gift cards to “runners” who quickly spent the funds at Target stores in Los Angeles and Orange counties. They purchased a variety of items including expensive electronics, other gift cards and more.
“The rapid transactions prevented victims from recouping the value on the cards when they contacted Target to report the scam,” authorities said.
“These defendants were part of a sophisticated, transnational fraud operation that targeted mostly older adults to cheat them out of their savings,” said U.S. Attorney Martin Estrada of the Central District of California. “Protecting our most vulnerable community members is critically important, and we will hold accountable those who reach into our country to engage in these sorts of egregious fraud schemes.”
Bai was found guilty of two counts of conspiracy to commit money laundering and was sentenced to 15 years in prison. He was ordered to pay $97,815 in restitution.
Bai was arrested in November 2020 on a criminal complaint involving this case and was released on bond. Within days of his release, authorities said he engaged in yet another money laundering scheme involving Target gift cards. He was arrested in February 2022 and has remained in federal custody since.
Hu was sentenced to 10 years in federal prison and ordered to pay $57,156 in restitution. Shi was sentenced to eight years and ordered to pay $39,416 in restitution.
One of the runners, Yan Fu, 60, of Chino Hills, pleaded guilty in September 2022 to one count of conspiracy to commit money laundering. He is serving a 20-month sentence in prison and was ordered to pay $48,073 in restitution.
“This case offers an important reminder to consumers that gift cards are for presents to friends and loved ones – they should never be used for payments to any government or corporate entity,” said Acting U.S. Attorney Tracy L. Wilkison in the 2021 indictment. “Don’t be fooled by callers claiming to be with a government agency, a bank or any other institution demanding that you purchase gift cards. There is no reason to purchase a gift card to resolve a problem with an account, your Social Security number or a supposed criminal case.”
Anyone who is age 60 or older and has experienced financial fraud can seek help by calling the National Elder Fraud Hotline at 1-833-372-8311.
To report a gift card scam, contact the FBI’s Internet Crime Complaint Center or the Federal Trade Commission. The public can also call 877-382-4357 or their local police department.
—
(司法部新闻稿)
PRESS RELEASE
Los Angeles Trio Sentenced for Laundering Gift Cards Purchased by Victims of Telephone Scams
Tuesday, March 26, 2024
For Immediate Release
Office of Public Affairs
A California man and two Chinese nationals were sentenced today to 15, 10 and eight years in prison, respectively, for laundering gift cards purchased by telephone-scam fraud victims at Target stores across the United States.
According to court documents, Blade Bai, 35, of El Monte, Bowen Hu, 28, of Hacienda Heights, California, and Tairan Shi, 29, of Diamond Bar, California, were part of a network of individuals who laundered proceeds of fraud stored on Target gift cards. Telephone scammers fraudulently induced victims across the country to buy gift cards, often $500 each, and to provide the card numbers and access codes to the scammers. The scammers included government imposters falsely claiming to be police and other government personnel and retail and tech support impersonators falsely offering to fix nonexistent issues with the victims’ online account or computer.
The defendants acquired more than 5,000 gift card numbers and access codes from a group in the People’s Republic of China calling itself the “Magic Lamp,” and funneled the gift cards to “runners” to liquidate at Target stores in southern California. Those runners, at the defendants’ direction, would quickly use the cards to purchase high-value consumer electronics and conduct other transactions. The rapid transactions prevented Target from recouping the value on the cards for the original victim-purchasers.
A jury convicted the defendants of a money laundering conspiracy that spanned from approximately June 2019 to November 2020. The jury also convicted Bai of a second money laundering conspiracy, in which he enlisted an associate to help sell a batch of gift cards with fraudulent proceeds after his initial arrest in the case. One of the defendants’ main “runners,” Yan Fu, 61, of Chino Hills, California, pleaded guilty and was previously sentenced to 20 months in federal prison.
“Transnational fraud schemes typically rely on complicated networks designed to launder victim proceeds,” said Principal Deputy Assistant Attorney General Brian M. Boynton, head of the Justice Department’s Civil Division. “This case is a testament to the commitment of the department and our partners to ensuring that all those who knowingly facilitate fraud face justice.”
“These defendants were part of a sophisticated, transnational fraud operation that targeted mostly older adults to cheat them out of their savings,” said U.S. Attorney Martin Estrada for the Central District of California. “Protecting our most vulnerable community members is critically important, and we will hold accountable those who reach into our country to engage in these sorts of egregious fraud schemes.”
“The FBI and its partners are committed to going after networks that perpetuate fraud even when they are targeting the American people from thousands of miles away and over the phone,” said Executive Assistant Director Timothy Langan of the FBI’s Criminal, Cyber, Response and Services Branch. “Today’s sentencing should make it known to individuals that participate in this sort of illegal activity that they can expect to face the consequences of their actions.”
“HSI Los Angeles’ El Camino Real Financial Crimes Task Force will continue to aggressively target greedy criminals and organizations that seek to line their pockets by defrauding unsuspecting victims,” said Special Agent in Charge Eddy Wang for HSI Los Angeles. “The defendants’ desire for easy money will lead to them doing hard time.”
Homeland Security Investigations’ El Camino Real Financial Crimes Task Force and the FBI investigated the case, with assistance from the Social Security Administration’s Office of the Inspector General and numerous local police departments across the United States, including the Brea Police Department, La Palma Police Department and Menifee Police Department. The El Camino Real Financial Crimes Task Force is part of HSI’s National El Dorado Task Force Initiative and is a multi-agency task force comprised of federal and state investigators focused on financial crimes in Southern California.
Assistant U.S. Attorney Monica E. Tait for the Central District of California and Trial Attorneys Wei Xiang and Meredith B. Healy of the Civil Division’s Consumer Protection Branch prosecuted the case.
If you or someone you know is age 60 or older and has experienced financial fraud, experienced professionals are standing by at the National Elder Fraud Hotline at 1-833-FRAUD-11 (1-833-372-8311). This Justice Department hotline, managed by the Office for Victims of Crime, can provide personalized support to callers by assessing the needs of the victim and identifying relevant next steps. Case managers will identify appropriate reporting agencies, provide information to callers to assist them in reporting, connect callers directly with appropriate agencies and provide resources and referrals, on a case-by-case basis. Reporting is the first step. Reporting can help authorities identify those who commit fraud and reporting certain financial losses due to fraud as soon as possible can increase the likelihood of recovering losses. The hotline is open Monday through Friday from 10:00 a.m. to 6:00 p.m. ET. English, Spanish and other languages are available.
—
(美国加州中区检察官办公室新闻稿)
PRESS RELEASE
Three Los Angeles County Men Sentenced to Federal Prison for Laundering Gift Cards Purchased by Victims of Telephone Scams
Tuesday, March 26, 2024
For Immediate Release
U.S. Attorney’s Office, Central District of California
LOS ANGELES – An El Monte man and two Chinese nationals living elsewhere in Los Angeles County were sentenced today to terms in federal prison for laundering gift cards purchased by telephone-scam fraud victims at Target stores across the United States.
Blade Bai, 35, of El Monte; Bowen Hu, 28, of Hacienda Heights; and Tairan Shi, 29, of Diamond Bar; were sentenced to terms of 15 years, 10 years, and eight years in federal prison, respectively.
United States District Judge André Birotte Jr. also ordered the defendants to pay restitution in the amounts of $97,815 for Bai, $57,156 for Hu, and $39,416 for Shi.
Bai has been in federal custody since February 2022. Hu and Shi were remanded into custody after the guilty verdicts against them were read in September 2023.
“These defendants were part of a sophisticated, transnational fraud operation that targeted mostly older adults to cheat them out of their savings,” said United States Attorney Martin Estrada of the Central District of California. “Protecting our most vulnerable community members is critically important, and we will hold accountable those who reach into our country to engage in these sorts of egregious fraud schemes.”
The defendants were part of a network of individuals who laundered proceeds of fraud stored on Target gift cards. Telephone scammers fraudulently induced victims across the country to buy gift cards, often $500 each, and to provide the card numbers and access codes to the scammers. The scammers included government imposters falsely claiming to be police and other government personnel and retail and tech support impersonators falsely offering to fix nonexistent issues with the victims’ online account or computer.
The defendants acquired more than 5,000 gift card numbers and access codes from a group in the People’s Republic of China calling itself the “Magic Lamp,” and funneled the gift cards to “runners” to liquidate at Target stores in Southern California. Those runners, at the defendants’ direction, would quickly use the cards to purchase high-value consumer electronics and conduct other transactions. The rapid transactions prevented victims from recouping the value on the cards when they contacted Target to report the scam.
At the conclusion of a 10-day trial in September 2023, a jury found the defendants guilty of a money laundering conspiracy that spanned from approximately June 2019 to November 2020. The jury also found Bai guilty of a second money laundering conspiracy, in which he enlisted an associate to help sell a batch of gift cards with fraudulent proceeds after his initial arrest in the case. One of the defendants’ main “runners,” Yan Fu, 61, of Chino Hills, pled guilty and was previously sentenced to 20 months in federal prison.
“Transnational fraud schemes typically rely on complicated networks designed to launder victim proceeds,” said Principal Deputy Assistant Attorney General Brian M. Boynton, head of the Justice Department’s Civil Division. “This case is a testament to the commitment of the department and our partners to ensuring that all those who knowingly facilitate fraud face justice.”
“The FBI and its partners are committed to going after networks that perpetuate fraud even when they are targeting the American people from thousands of miles away and over the phone,” said Executive Assistant Director Timothy Langan of the FBI’s Criminal, Cyber, Response and Services Branch. “Today’s sentencing should make it known to individuals that participate in this sort of illegal activity that they can expect to face the consequences of their actions.”
“HSI Los Angeles’ El Camino Real Financial Crimes Task Force will continue to aggressively target greedy criminals and organizations that seek to line their pockets by defrauding unsuspecting victims,” said Special Agent in Charge Eddy Wang for HSI Los Angeles. “The defendants’ desire for easy money will lead to them doing hard time.”
The Los Angeles Field Offices of Homeland Security Investigations and the FBI investigated the case, with assistance from the Social Security Administration’s Office of the Inspector General and numerous local police departments across the United States, including the Brea Police Department, the La Palma Police Department, and the Menifee Police Department.
Assistant United States Attorney Monica E. Tait of the Major Frauds Section and Trial Attorneys Wei Xiang and Meredith B. Healy of the Justice Department’s Consumer Protection Branch prosecuted the case.
If you or someone you know is age 60 or older and has experienced financial fraud, experienced professionals are standing by at the National Elder Fraud Hotline: 1-833-FRAUD-11 (1-833-372-8311). This U.S. Department of Justice hotline, managed by the Office for Victims of Crime, can provide personalized support to callers by assessing the needs of the victim and identifying relevant next steps. Case managers will identify appropriate reporting agencies, provide information to callers to assist them in reporting, connect callers directly with appropriate agencies, and provide resources and referrals, on a case-by-case basis. Reporting is the first step. Reporting can help authorities identify those who commit fraud and reporting certain financial losses due to fraud as soon as possible can increase the likelihood of recovering losses. The hotline is open Monday through Friday from 7 a.m. to 3 p.m. PT. English, Spanish and other languages are available.
2024.3.26,全球最大的加密货币交易所之一“库币”(KuCoin)面临美国纽约南区检察官指控的刑事诉讼和美国商品期货交易委员会指控的民事强制执行诉讼
KuCoin及其两位创始人Chun Gan和Ke Tang无视美国反洗钱法,将KuCoin发展成为全球最大的加密货币交易所之一
Gan,34岁和Tang,39岁,均为中国公民,各自被指控一项共谋违反《银行保密法》的罪名和一项共谋经营无牌汇款业务的罪名。GAN 和 TANG 仍然逍遥法外。
美国检察官达米安·威廉姆斯 (Damian Williams) 表示:“正如今天的起诉书所指控的那样,KuCoin 及其创始人故意隐瞒大量美国用户在 KuCoin 平台上进行交易的事实。事实上,据称库币利用其庞大的美国客户群,成为全球最大的加密货币衍生品和现货交易所之一,日交易量达数十亿美元,年交易量达数万亿美元。但像 KuCoin 这样利用美国独特机会的金融机构也必须遵守美国法律,以帮助识别和消除犯罪和腐败融资计划。据称,库币故意选择不这样做,被告甚至未能执行基本的反洗钱政策,导致库币在金融市场的阴影下运作,并被用作非法洗钱的避风港,库币收受超过 50 亿美元,汇出超过 40 亿美元可疑和犯罪资金。像 KuCoin 这样的加密货币交易所不能两者兼得。今天的起诉书应该向其他加密货币交易所发出一个明确的信息:如果你计划为美国客户提供服务,你必须遵守美国法律,简单明了。”
商品期货交易委员会今天宣布,已向 美国纽约南区地方法院 提起民事强制执行诉讼,KuCoin是一家中心化数字资产交易所,多次违反《商品交易法》(CEA)和 CFTC 法规。起诉书指控 KuCoin非法从事场外商品期货交易以及杠杆、保证金或融资零售商品交易;未在 CFTC 注册为期货佣金商 (FCM) 的情况下征求并接受商品期货、掉期以及杠杆、保证金或融资零售商品交易的订单;未能认真监督其 FCM 活动;经营掉期交易或处理设施,但未在 CFTC 注册为掉期执行设施 (SEF) 或指定合约市场 (DCM);未能实施有效的客户识别计划(CIP)。 在针对 KuCoin 的持续诉讼中,CFTC 寻求归还非法所得、民事罚款、永久交易和注册禁令,以及针对进一步违反 CEA 和 CFTC 规定的行为发出永久禁令。
KuCoin发言人在一封电子邮件中表示,该交易所已了解相关报道,正在通过律师调查细节,并补充说,该交易所尊重“各国法律法规,严格遵守合规标准”。
KuCoin首席执行官Johnny Lyu在X上发帖回应了这些指控,他表示:“与KuCoin相关的监管问题引起了我的注意。在我们处理此问题期间,平台不受影响并且正常运行。您的资产在我们这里是安全无虞的。”
根据首席执行官 Johnny Lyu 3 月 27 日在该交易所博客上发布的一封信,“我谨向所有KuCoin用户表示感谢,感谢你们在过去几天里的支持、信任和陪伴。”
Lyu 继续说道:“近期,3月26日至27日,部分用户出现提现等待时间超预期的情况。 […]为表达对您的支持和耐心的深切感谢,KuCoin将推出总额为1000万美元的KCS和BTC特别空投活动。”
Lyu写道,空投规则将在三天内发布。最近提款的延迟可能是由于谨慎的客户放弃交易所而造成的高交易量造成的。因此,空投奖励了在危机时期仍然忠于交易所的用户。
此次空投的时机值得注意,因为库币一天前就遭到了一系列法律诉讼。
空投是有风险的,其中最重要的是可能采取监管行动。 SEC在其文件《数字资产“投资合约”分析框架》中写道:“数字资产缺乏货币考虑,例如通过所谓的‘空投’分配的数字资产,空投可能构成证券的销售或分配。”
数据公司 CoinMarketCap 的数据显示,在加密货币现货交易所中,KuCoin 在流量、流动性和交易量等方面落后于 Binance、Coinbase 和 Kraken。
KuCoin and Its Founders Face Criminal Charges Over Money-Laundering Violations
Prosecutors also allege the cryptocurrency exchange operated an unlicensed money-transmitting business
U.S. prosecutors have filed criminal charges against KuCoin and two of its founders, accusing the global cryptocurrency exchange of violating U.S. anti-money-laundering laws.
The indictment, unsealed Tuesday by prosecutors in Manhattan, charged KuCoin with violating the Bank Secrecy Act and operating an unlicensed money transmitting business, along with related conspiracy charges. Prosecutors also charged two of KuCoin’s founders, Chun Gan and Ke Tang, with related conspiracy charges.
The U.S. Commodity and Futures Trading Commission, the derivatives market regulator, on Tuesday filed parallel civil charges against KuCoin for operating as an illegal digital asset derivatives exchange and for multiple violations of the Commodity Exchange Act.
Gan and Tang, both Chinese citizens, each face up to 10 years in prison if convicted on the charges.
A spokesperson for KuCoin in an email said the exchange is aware of the related reports and is investigating the details through its lawyers, adding it respects the “laws and regulations of various countries and strictly adheres to compliance standards.”
KuCoin Chief Executive Johnny Lyu addressed the charges in a post on X, saying “the regulatory matter related to KuCoin has come to my attention. While we’re working on it, the platform is unaffected and operating normally as usual. Your assets are safe and sound with us.”
Efforts to reach Gan and Tang for comment Tuesday weren’t successful. It remains unclear if they have obtained legal representation.
Prosecutors in the U.S. Attorney’s Office for the Southern District of New York alleged KuCoin intentionally failed to have an adequate anti-money-laundering program to prevent the exchange from being used for terrorist financing and other illicit finance activities.
The exchange also allegedly failed to maintain reasonable procedures to verify the identities of customers and to file suspicious activity reports, or SARs, as required.
As a result of the anti-money-laundering control failures, prosecutors said many customers sought out KuCoin for the anonymity of its services and alleged the exchange received over $5 billion and sent over $4 billion in suspicious and criminal proceeds since 2017.
Gan and Tang founded KuCoin in September 2017 as a spot trading platform and launched a derivatives trading platform in 2019. The crypto exchange is operated collectively by a few entities, including PhoenixFin, Flashdot and Peken Global.
Since its founding, KuCoin has grown to service more than 30 million customers with billions of dollars’ worth of crypto in daily trading volume, according to the Justice Department.
Prosecutors alleged KuCoin solicited business from U.S. customers and served numerous people located in the U.S. But the exchange failed to register with the CFTC as a futures commission merchant, and through at least the end of 2023 it failed to register with the U.S. Treasury Department’s Financial Crimes Enforcement Network as a money transmitting business, as required of crypto exchanges.
KuCoin, Gan and Tang were aware of their U.S. compliance requirements but chose to flout them, prosecutors said. Until they were notified of a federal criminal investigation into KuCoin’s activities last July, the exchange didn’t have a know-your-customer program. KuCoin then required new customers to provide identifying information but didn’t apply the process to earlier customers.
Tuesday’s charges are the latest regulatory problems for KuCoin. The exchange in December agreed to pay $22 million and to stop doing business in New York to settle a lawsuit brought by the state’s attorney general’s office in March 2023 after admitting it operated as an unregistered exchange in the state.
—
Prominent Global Cryptocurrency Exchange KuCoin And Two Of Its Founders Criminally Charged With Bank Secrecy Act And Unlicensed Money Transmission Offenses
Tuesday, March 26, 2024
For Immediate Release
U.S. Attorney’s Office, Southern District of New York
KuCoin and Two of Its Founders, Chun Gan and Ke Tang, Flouted U.S. Anti-Money Laundering Laws to Grow KuCoin Into One of World’s Largest Cryptocurrency Exchanges
Damian Williams, the United States Attorney for the Southern District of New York, and Darren McCormack, the Acting Special Agent in Charge of the New York Field Office of Homeland Security Investigations (“HSI”), announced today the unsealing of an Indictment against global cryptocurrency exchange KuCoin and two of its founders, CHUN GAN, a/k/a “Michael,” and KE TANG, a/k/a “Eric,” for conspiring to operate an unlicensed money transmitting business and conspiring to violate the Bank Secrecy Act by willfully failing to maintain an adequate anti-money laundering (“AML”) program designed to prevent KuCoin from being used for money laundering and terrorist financing, failing to maintain reasonable procedures for verifying the identity of customers, and failing to file any suspicious activity reports. KuCoin was also charged with operating an unlicensed money transmitting business and a substantive violation of the Bank Secrecy Act. GAN and TANG remain at large.
U.S. Attorney Damian Williams said: “As today’s Indictment alleges, KuCoin and its founders deliberately sought to conceal the fact that substantial numbers of U.S. users were trading on KuCoin’s platform. Indeed, KuCoin allegedly took advantage of its sizeable U.S. customer base to become one of the world’s largest cryptocurrency derivatives and spot exchanges, with billions of dollars of daily trades and trillions of dollars of annual trade volume. But financial institutions like KuCoin that take advantage of the unique opportunities available in the United States must also comply with U.S. law to help identify and drive out crime and corrupt financing schemes. KuCoin allegedly deliberately chose not to do so. As alleged, in failing to implement even basic anti-money laundering policies, the defendants allowed KuCoin to operate in the shadows of the financial markets and be used as a haven for illicit money laundering, with KuCoin receiving over $5 billion and sending over $4 billion of suspicious and criminal funds. Crypto exchanges like KuCoin cannot have it both ways. Today’s Indictment should send a clear message to other crypto exchanges: if you plan to serve U.S. customers, you must follow U.S. law, plain and simple.”
HSI Acting Special Agent in Charge Darren McCormack said: “Today, we exposed one of the largest global cryptocurrency exchanges for what our investigation has found it to truly be: an alleged multibillion-dollar criminal conspiracy. KuCoin grew to service over 30 million customers, despite its alleged failure to follow laws necessary to ensuring the security and stability of our world’s digital banking infrastructure. The defendants’ alleged pattern of skirting these vitally important laws has finally come to an end. I commend HSI New York’s El Dorado Task Force and our law enforcement partners for their commitment to the mission.”
According to the allegations in the Indictment and KuCoin’s statements on its website:[1]
FLASHDOT LIMITED, formerly known as “Phoenixfin Limited,” PEKEN GLOBAL LIMITED, and PHOENIXFIN PRIVATE LIMITED are three entities collectively doing business as global cryptocurrency exchange KuCoin. GAN and TANG, among others, founded KuCoin in September 2017.
KuCoin solicited business from U.S. customers through its spot trading platform and, later, its futures trading platform, which was launched in July 2019. Since its founding in 2017, KuCoin has become one of the largest global cryptocurrency exchange platforms, with more than 30 million customers and billions of dollars’ worth of cryptocurrency in daily trading volume. KuCoin’s website touts public rankings of cryptocurrency exchanges that place KuCoin in the top five worldwide. One of these public rankings listed KuCoin as the fourth largest cryptocurrency derivatives exchange and fifth largest cryptocurrency spot exchange. KuCoin, GAN, and TANG sought to serve, and have in fact served, numerous customers located in the United States and in the Southern District of New York.
As a result, at all relevant times, KuCoin has been a money transmitting business required to register with the U.S. Department of Treasury’s Financial Crimes Enforcement Network (“FinCEN”) and, since July 2019, has been a futures commission merchant required to register with the U.S. Commodity and Futures Trading Commission (“CFTC”). As a money transmitting business and a futures commission merchant, KuCoin is required to comply with the applicable Bank Secrecy Act provisions requiring maintenance of an adequate AML program, including customer identity verification, or know-your-customer (“KYC”) processes. AML and KYC programs ensure that financial institutions, such as KuCoin, are not used for illicit purposes, including money laundering.
GAN, TANG, and KuCoin were aware of their U.S. AML obligations but willfully chose to flout those requirements. KuCoin failed, for example, to implement an adequate KYC program. Indeed, until at least July 2023, KuCoin did not require customers to provide any identifying information. It was only in July 2023, after KuCoin was notified of a federal criminal investigation into its activities, that KuCoin belatedly adopted a KYC program for new customers. However, this KYC process applied to new customers only and did not apply to KuCoin’s millions of existing customers, including the substantial number of customers based in the United States. KuCoin also never filed any required suspicious activity reports, never registered with the CFTC as a futures commission merchant, and, through at least the end of 2023, never registered with FinCEN as a money transmitting business.
In fact, GAN, TANG, and KuCoin affirmatively attempted to conceal the existence of KuCoin’s U.S. customers in order to make it appear as if KuCoin was exempt from U.S. AML and KYC requirements. Despite the fact that KuCoin gathered and tracked location information for its customers, KuCoin actively prevented its U.S. customers from identifying themselves as such when opening KuCoin accounts. And KuCoin lied to at least one investor, in 2022, about where its customers were located, falsely representing that it had no U.S. customers when, in truth, KuCoin had a substantial U.S. customer base. In fact, in a number of social media posts, KuCoin actively marketed itself to U.S. customers as an exchange where they could trade without having to undergo KYC. For example, KuCoin stated in an April 2022 message on Twitter that “KYC is not supported to USA users, however, it is not mandatory on KuCoin to do KYC. Usual transactions can be done using an unverified account-”
As a result of KuCoin’s willful failures to maintain the required AML and KYC programs, KuCoin has been used as a vehicle to launder large sums of criminal proceeds, including proceeds from darknet markets and malware, ransomware, and fraud schemes. Since its founding in 2017, KuCoin has received over $5 billion, and sent over $4 billion, of suspicious and criminal proceeds. Many KuCoin customers used its trading platform specifically because of the anonymity of the services it provided. In other words, KuCoin’s no-KYC policy was integral to its growth and success.
*
GAN, 34, and TANG, 39, both citizens of China, are each charged with one count of conspiring to violate the Bank Secrecy Act and one count of conspiring to operate an unlicensed money transmitting business, each of which carries a maximum sentence of five years in prison.
FLASHDOT LIMITED, an entity incorporated in the Cayman Islands; PEKEN GLOBAL LIMITED, an entity incorporated in the Republic of Seychelles; and PHOENIXFIN PRIVATE LIMITED, an entity incorporated in Singapore, together d/b/a “KuCoin,” are each charged with one count of conspiring to violate the Bank Secrecy Act, which carries a maximum sentence of five years in prison; one count of conspiring to operate an unlicensed money transmitting business, which carries a maximum sentence of five years in prison; one count of violating the Bank Secrecy Act, which carries a maximum sentence of 10 years in prison; and one count of operating an unlicensed money transmitting business, which carries a maximum sentence of five years in prison.
The maximum potential sentences in this case are prescribed by Congress and are provided here for information purposes only, as any sentencing of the defendants will be determined by the judge.
Mr. Williams praised the outstanding investigative work of HSI New York’s El Dorado Task Force. Mr. Williams further thanked the Commodity Futures Trading Commission, which today filed a parallel civil action against KuCoin.
This matter is being handled by the Office’s Illicit Finance & Money Laundering Unit. Assistant U.S. Attorneys Emily Deininger and David R. Felton are in charge of the prosecution.
The charges contained in the Indictment are merely accusations, and the defendants are presumed innocent unless and until proven guilty.
—
Release Number 8884-24
CFTC Charges KuCoin with Operating Illegal Digital Asset Derivatives Exchange
March 26, 2024
Washington, D.C. — The Commodity Futures Trading Commission today announced it filed a civil enforcement action in the U.S. District Court for the Southern District of New York charging Mek Global Limited, PhoenixFin PTE Ltd., Flashdot Limited, and Peken Global Limited, which collectively operate a centralized digital asset exchange under the name KuCoin, with multiple violations of the Commodity Exchange Act (CEA) and CFTC regulations.
The complaint charges KuCoin illegally dealt in off-exchange commodity futures transactions and leveraged, margined, or financed retail commodity transactions; solicited and accepted orders for commodity futures, swaps, and leveraged, margined, or financed retail commodity transactions without registering with the CFTC as a futures commission merchant (FCM); failed to diligently supervise its FCM activities; operated a facility for the trading or processing of swaps without registering with the CFTC as a swap execution facility (SEF) or designated contract market (DCM); and failed to implement an effective customer identification program (CIP).
In its continuing litigation against KuCoin, the CFTC seeks disgorgement, civil monetary penalties, permanent trading and registration bans, and a permanent injunction against further violations of the CEA and CFTC regulations, as charged.
“For too long, some offshore crypto exchanges have followed a now-familiar playbook by offering derivative products and falsely claiming people in the United States cannot use their platforms, when in reality, anyone in the U.S. with commonly used technology can trade without providing basic customer identifying information,” said Director of Enforcement Ian McGinley.
“As made clear by the CFTC’s action today and its previous enforcement actions, the CFTC’s playbook should also now be familiar – the CFTC will charge such entities with failing to register with the CFTC and failing to comply with the agency’s rules that protect U.S. customers and prevent and detect terrorist financing and money laundering,” McGinley continued.
Case Background
According to the complaint, KuCoin offered and executed commodity derivatives and leveraged, margined, or financed commodity transactions to and for people in the U.S. from approximately July 2019 to approximately June 2023, and failed to implement required know-your-customer (KYC) compliance procedures. The complaint further alleges that although KuCoin claimed to have implemented KYC procedures, those procedures were a sham and did not prevent U.S. customers from trading commodity interests and derivatives on the platform.
The complaint also alleges people who identified themselves as being U.S. customers were permitted to trade commodity futures, swaps, and leveraged, margined, or financed commodity transactions on the exchange, in violation of the CEA and CFTC regulations. KuCoin failed to impose any IP address restrictions during the relevant period to prevent U.S. customers from trading commodity interests or account for commonly used technology such as virtual private networks (VPNs) that could potentially circumvent IP address restrictions.
Related Criminal Action
In a separate criminal matter, the U.S. Attorney’s Office for the Southern District of New York filed an indictment against PhoenixFin PTE Ltd., Flashdot Limited, and Peken Global Limited charging them with violating the Bank Secrecy Act, operating an unlicensed money transmitter business, and conspiracy to violate the Bank Secrecy Act and operate as an unlicensed money transmitter business.
*
The Division of Enforcement staff responsible for this matter are Christopher Giglio, Andrew Rodgers, Jack Murphy, K. Brent Tomer, Lenel Hickson, Jr., and Manal M. Sultan.
*
The CFTC also strongly urges the public to verify a company’s registration with the CFTC before committing funds. If unregistered, a customer should be wary of providing funds to that company. A company’s registration status can be found using NFA BASIC.
Customers and other individuals can report suspicious activities or information, such as possible violations of commodity trading laws, to the Division of Enforcement via a toll-free hotline 866-FON-CFTC (866-366-2382)), file a tip or complaint online, or contact the Whistleblower Office. Whistleblowers may be eligible to receive between 10 and 30 percent of the monetary sanctions collected paid from the CFTC Customer Protection Fund financed through monetary sanctions paid to the CFTC by violators of the CEA.
—
KuCoin plans $10M airdrop of BTC, KCS as Justice Dept., CFTC circle
The crypto exchange is sweetening the deal for loyal customers as it faces new legal challenges.
Cryptocurrency exchange KuCoin will hold an airdrop of Bitcoin BTC and its native KuCoin (KCS) token worth $10 million, according to a letter from CEO Johnny Lyu posted on the exchange’s blog on March 27. The news comes a day after the United States Justice Department announced charges against the exchange and two of its founders.
Lyu did not mention the federal charges, although he alluded to them in the first sentence of his letter:
“I would like to express my gratitude to all KuCoin users, for your support, trust and companionship during the past few days.”
Comparing the airdrop to the exchange’s reimbursement of its investors who lost money in the Confido rug pull, Lyu continued:
“Recently, on March 26th and 27th, some users experienced longer-than-expected wait times during the withdrawal process. […] To express our profound gratitude for your support and patience KuCoin will launch a special airdrop event totaling 10 million USD in KCS and BTC.”
Rules for the airdrop will be released in three days, Lyu wrote. The recent delays in withdrawals were possibly caused by the high volume as wary customers abandoned the exchange. The airdrop thus rewards users who remained loyal to the exchange in its time of crisis.
The timing of the airdrop is noteworthy since KuCoin was hit with a barrage of legal actions one day earlier. The Justice Department unsealed an indictment for violations of the Bank Secrecy Act for lacking an Anti-Money Laundering program by the two founders and operating an unlicensed money-transmitting business.
Simultaneously, the Commodity Futures Trading Commission (CFTC) initiated a civil case against the exchange for violations of the Commodity Exchange Act and CFTC regulations.
KuCoin hastened to assure users that their assets were safe after the charges were filed and KCS fell 12% in 24 hours.
Airdrops come with risks, not the least of which is the possibility of regulatory action. The SEC wrote in its document “Framework for “Investment Contract” Analysis of Digital Assets”:
“The lack of monetary consideration for digital assets, such as those distributed via a so-called ‘air drop,’ does not mean that the investment of money prong [of the Howey test] is not satisfied; therefore, an airdrop may constitute a sale or distribution of securities.”
The DeFi Education Fund teamed up with a small Texas clothing company sued for a declaratory judgment against the SEC to prevent the agency from prosecuting the company for holding an airdrop.
2024.3.22,(马里兰州蒙哥马利县)一名加州男子在蒙哥马利县被捕,警方称他通过一项涉及冒充政府官员的计划以老年人为目标实施诈骗。
蒙哥马利县警察局 (MCDP) 表示,警方于 3 月 18 日星期一逮捕了来自加利福尼亚州阿伯湖的 34 岁的孙文辉 (Wenhui Sun)。
MCDP 表示,一名受害者于 3 月初首次向警方报告了这起盗窃案。她报告说,一名自称联邦贸易委员会监察长办公室工作人员联系了她,并表示她是身份盗窃的受害者。警方称,来电者告诉这名女子,这起盗窃案“导致联邦调查涉及毒品和洗钱”。
打电话的人告诉该女子将她的所有资产转入金条,“联邦调查局特工”将接走金条并将其带到美国财政部。受害者这样做了,并分两次将金条交给了快递员。
MCDP 表示,这些金条总价值超过 789,000 美元。
警方称,一名 60 多岁的便衣侦探冒充诈骗受害者来抓捕涉嫌诈骗的人。调查人员让这名女子继续与骗子沟通,告诉他们她有更多金条,以引诱他们回来,尽管警方担心骗子可能会识破这个诡计。但这一做法奏效了,欺诈者表示他们将返回。周一晚上 7 点刚过,孙驾驶一辆黑色吉普车到达。
警方称,孙被逮捕,被带入监狱,并受到指控,目前被关押,不得保释。
警方在新闻稿中表示:“侦探们认为可能还有更多受害者,并希望提醒社区,执法部门绝不会尝试以这种方式与您联系。”
MONTGOMERY COUNTY
California man helped steal more than $789K in gold from elderly woman, Montgomery County police say
MONTGOMERY COUNTY, Md. (DC News Now) — A California man was arrested in Montgomery County after police say he targeted elderly people through a scheme that involved impersonating a government official.
The Montgomery County Department of Police (MCDP) said that officers arrested 34-year-old Wenhui Sun of Lake Arbor, Calif. on Monday, March 18.
MCDP said a victim first told police about the theft in early March. She reported that a person who identified himself as being with the Office of the Inspector General – Federal Trade Commission had contacted her and said that she had been the victim of identity theft. The caller told the woman that the theft “led to a federal investigation involving drugs and money laundering,” police said.
The caller told the woman to transfer all of her assets into gold bars, which an “FBI agent” would pick up and take to the U.S. Department of Treasury. The victim did so and handed gold bars to the couriers in two separate deliveries.
MCDP said that the bars were worth over $789,000 in total.
Police identified Sun as the courier in the second gold bar delivery. Officers arrested him in Montgomery County around 7 p.m. on March 18 and transported him to the Central Processing Unit.
MCDP found a plane ticket to California dated the day of his arrest in his belongings.
Police believe there may be more victims of this scheme, and MCDP issued a reminder that “law enforcement will never attempt to contact you in this manner.” You can find more information and resources, including how to report a situation, online.
Anyone with any information is asked to head online or call 1-866-411-8477.
—
Imposter In $789K Gold Bar Scam Charged In MD: Police
The man was accused of posing as a member of the Federal Trade Commission and scamming a woman out of thousands of dollars.
GAITHERSBURG, MD — A 39-year-old California man was recently arrested in Montgomery County after authorities say he scammed a woman out of $789,000 worth of gold bars.
Wenhui Sun, of Lake Arbor, posed this month as a member of the Office of the Inspector General – Federal Trade Commission, the Montgomery County Police Department said Friday.
Sun was accused of telling the woman she had been the victim of an identity theft that led to a federal investigation involving drugs and money laundering, police said.
He was then accused of directing the woman to transfer her assets, worth $789,000, into two gold bars. Police said Sun told her the bars would retrieved by a courier who was an FBI agent, and who would take the bars to the U.S. Department of Treasury for safekeeping.
The woman complied with the instructions she was given, police said.
“Through the course of the investigation, detectives were able to identify Sun as the courier of the second delivery of gold bars,” police said in a news release.
Sun was arrested around 7 p.m. Monday in Montgomery County and was taken to jail, where he was charged and is being held without bond, police said.
“Detectives believe there may be additional victims and want to remind the community that law enforcement will never attempt to contact you in this manner,” police said in the release.
Anyone with information about Sun or this crime is asked to report it via the Crime Solvers of Montgomery County, MD website at www.crimesolversmcmd.org and click on the www.p3tips.com link at the top of the page or call 1-866-411-8477.
A reward of up to $10,000 is offered for information leading to the suspect’s arrest. Tips may remain anonymous.
—
A woman lost $789K in a gold bar scam, police say. Then she turned the tables.
Police say an undercover detective posed as a fraud victim in her 60s to catch the alleged scammer
Lisa Bromley has done a lot during her 30 years as a police officer in suburban Maryland. Undercover drug buys. Armed robbery investigations. Working car crashes.
But it wasn’t until last week that she found herself disguised in a wig and a coronavirus mask, playing the role of a scam victim in her 60s who police say had already been bilked out of about $789,000 worth of gold bars. Her hope: Their target would soon pull into a parking lot in Montgomery County’s sprawling Leisure World community looking for more gold.
The plan worked, law enforcement officials said in a news release Friday announcing the arrest of Wenhui Sun, 34, of Lake Forest , Calif. Local and federal authorities say his scam was part of a growing trend by swindlers. Often posing as federal investigators, they persuade their targets to buy gold bars — and turn them over for safekeeping — while purported investigators try to identify thieves who might otherwise have raided the target’s bank accounts.
“They’re doing anything they can to get to these people,” said Bromley, who has spent the past decade as a financial crimes investigator and worked a similar case last year in which the victim lost more than $1 million. “It breaks your heart.”
The scammers project both concern and subtle force, suggesting that if their targets don’t act quickly, they’ll not only lose their savings, but they’ll also miss out on a chance to help the government take down dangerous identity thieves. “Once the victim is on the hook, the scammer will keep going,” said FBI Supervisory Special Agent Keith Custer, who works such cases out of the bureau’s Baltimore field office.
Victims of the gold bar and related scams can be otherwise perfectly smart, Custer said. “Doctors, lawyers, executives. I’ve seen pretty much any victim.”
Sun is being held without bond in the Montgomery County jail and is charged with theft over $100,000 and attempted theft over $100,000, according to court records. Sun’s attorney could not be reached.
For Bromley and her colleagues in the Montgomery County police financial crimes section, the case began on March 10, when a woman called to report that she thought she had been swindled. The woman, whom police identified as Victim 1 in court filings to protect her privacy, said that in February, she received a phone call from a man who identified himself as “Mark Cooper” from “the Office of the Inspector General, Federal Trade Commission,” detectives wrote in a court affidavit.
The purported Mark Cooper told the woman she had been the victim of identity theft that had led to a federal drug and money laundering probe. The man then put the woman in contact with someone who identified himself as “Officer David Freeman,” who said he could provide her with a new Social Security number and witness protection, but only at the conclusion of his investigation, after she had fully cooperated, according to the affidavit.
“To ensure her cooperation and secure her assets, Victim 1 was directed to purchase gold bars,” detectives wrote, “which were to be turned over to FBI agents who would get the bars and place them into the U.S. Department of Treasury.”
Evoking the protection of an asset like gold is key to such schemes, said Custer, the FBI agent: “They like to conjure up Federal Reserve banks, images of stacks of gold at Fort Knox.”
And there is another reason they want their targets to order gold bars — usually done through wire transfers to legitimate sellers who then ship the gold via guaranteed parcel. Once the gold arrives, Custer said, the swindlers need only to persuade their targets to hand it over — a strategy that avoids the victim having to physically go into a bank to withdraw money, which can raise the suspicions of alert tellers and bankers.
In the Montgomery County case, the victim wired her first payment of $331,817.54 to a gold dealer on Feb. 21. Two weeks later, as she stayed in touch with the scammers with screenshots of her order status, the gold bars arrived via UPS, according to court records.
The scammers then told her to meet a “courier” near a parking lot outside Leisure World. She did so, placing the boxed-up gold in the back of the courier’s car, which then drove away.
Police say the scammers struck again the next day, persuading the woman to wire $457,410.34 to a gold dealer for more gold bars. On March 8, she again met the courier, this time at a nearby but different parking lot, and handed over the second package. The driver, behind the wheel of a Dodge Ram truck bearing New York license plates, drove away.
Two days later, realizing she had been scammed, the woman called police.
Video surveillance near the parking lot, detectives wrote, revealed the truck’s license plate, which they traced to a rental car company in New York and then to Sun, according to detectives. Automated license plate readers, they added, also tracked the truck driving from New York to Maryland on the day of the second gold bar pickup.
Investigators had the woman continue to communicate with the scammers, telling them she had more gold bars, to lure them back, even as police worried the scammers might sniff out the ruse. “I was extremely nervous,” said Detective Sean Petty. “This is their job. They have perfected this.”
But it worked, they wrote in court papers, saying the fraudsters indicated they would return for a new shipment.
This time, they were waiting — a team of financial crimes detectives and undercover officers including Bromley, wearing her mask and brunette wig, which she had had overnighted from Amazon. Just past 7 p.m. on Monday, a black Jeep Wagoneer — driven by Sun — arrived at the Leisure World guard booth and was let through, according to detectives.
He stopped at the meeting spot, according to detectives, at which point Bromley placed a brown box — valueless — on the back seat. The Wagoneer drove away, but not for long — undercover officers swarmed it a short time later.
Sun spoke to investigators, according to court records, saying a friend in China had directed him to drive to Maryland to pick up a package. He said he had also picked up the package on March 8 but didn’t know what was in it.
“Sun admitted that he had traveled to Tennessee, Montana, New York and Maryland, but advised the only place he’s picked up packages is Maryland,” investigators wrote.
They also revealed in court filings something they found in Sun’s Wagoneer: a plane ticket for that day to California. Sun said that he had postponed the trip to get the package but that he would be leaving for California the next day. Instead, according to court records, he was placed in jail.
2024.3.13,根据2024 年 3 月 11 日提交的一份法律文件,美国法院已命令币安前首席执行官赵长鹏将其所有有效或过期护照移交给第三方。美国地区法官 A. 琼斯命令赵长鹏在剩余刑期中留在美国,并将任何旅行计划通知当局。赵长鹏被要求将加拿大护照交给第三方保管人,无论他去哪里需要身份证明,第三方保管人都必须陪同他。此外,该文件还指出,赵长鹏“未经法院许可,不得从任何国家申请或获得新护照或旅行证件”。持有赵长鹏护照的第三方必须在征得审前服务部门或法院许可后才能将护照返还给赵长鹏。
US court orders Binance founder, Changpeng Zhao to surrender all passports
A United States (US) district court has ordered the founder and former CEO of Binance, Changpeng Zhao to surrender all his passports to a third party and keep authorities updated on his travel plans.
The order was contained in a legal filing tendered on Tuesday, modifying Zhao’s bond conditions for release.
This development emerged following the US application to modify his bond requirements on March 5.
Bond conditions are court-enforced demands that a defendant on pretrial release must follow until his case is resolved under law.
As part of the bond, Richard Jones, a US district judge, ordered Zhao to remain in the US and notify court authorities of any travel arrangements.
“Defendant must remain in the continental United States through the imposition of sentence,” the judge said.
“Defendant must notify Pretrial Services before any travel within the continental United States.
“Defendant must surrender his current Canadian passport to a third-party custodian employed and supervised by his counsel of record. The third-party custodian must retain control over that Canadian passport and must accompany Defendant on any travel that requires identification documents.
“Defendant must surrender all other current and expired passports and travel documents to his counsel of record, who may return those documents to defendant only with authorisation from Pretrial Services or the Court. Defendant may not apply for or obtain a new passport or travel document from any country without the Court’s permission.”
2024.3.10,住址报纽约法拉盛45大道的梁飞(Fei Liang,音译)与一名同谋合伙进行电话诈骗,声称他来自社会安全局、银行或供应商,受害者的账户暴露了,要求受害人将钱汇到其它账户进行 “安全保管”,用这种手段骗走了全美多地的六名老人总共628,278美元。
MELINDA KATZ DISTRICT ATTORNEY PRESS RELEASE
QUEENS MAN CHARGED WITH SCAMMING MORE THAN $600,000 FROM SENIORS ACROSS U.S.
March 10, 2024
Queens District Attorney Melinda Katz announced that Fei Liang was charged with possession of stolen property in connection with a scheme that defrauded $628,278 from senior citizens across the country. Liang is alleged to have worked with a co-conspirator who called seniors and claimed to be from the Social Security Administration, their bank, or a vendor. He told the victims their accounts had been compromised and instructed the seniors to wire money to other accounts for “safekeeping.”
District Attorney Katz said: “At a time in their lives when they should be able to enjoy the fruits of their hard work, seniors are often victimized by ruthless scammers who leave them in financial ruin. We will continue to aggressively prosecute fraudsters and work to educate the public on how to defend against these predators.”
Homeland Security Investigations New York Acting Special Agent in Charge Erin Keegan said: “The defendant is accused of preying on the insecurities of vulnerable individuals who believed their Social Security numbers or other personal accounts had been compromised. As alleged, his deplorable crimes cost elderly victims upwards of $620,000 before he could be stopped. I commend HSI New York’s El Dorado Task Force Economic Crimes Group, the Queens District Attorney’s Office, HSI Baltimore and our law enforcement partners for their outstanding coordination. Today and always, we urge the public to be cautious of opportunists seeking to exploit their fears.”
Liang, 39, of 45th Avenue in Flushing, was arraigned on a complaint charging him with six counts of criminal possession of stolen property in the second degree and one count of attempted criminal possession of stolen property in the second degree.
Liang faces up to 15 years in prison if convicted. Judge Jeffrey Gershuny ordered him to return to court April 10.
According to the charges, Liang opened bogus corporate accounts, under the names JMG Aluminum, Inc., and New Century Aluminum, Inc., at three Queens banks: a TD Bank in Flushing and Capital One and Chase banks in Bayside. Liang listed himself as the president of the aluminum companies.
Between October 2022 and March 2023, wire transfers totaling $628,278.44 were made to Liang’s bank accounts from six victims as follows:
•On October 5, 2022, a victim from Trumbull, Connecticut, wired $190,000 after he received a pop-up message on his computer advising him to call Microsoft at a particular number. When the victim called, he was told that fraudulent activity had been observed on his computer and his bank account may have been compromised. To safeguard his money, the victim was advised to wire funds to another account—one that had been opened by Liang at a TD Bank in Flushing. That same day, withdrawals were made from the TD account.
•On January 31, 2023, a victim from Miami wired $96,300 after he was contacted by an individual purporting to be a Wells Fargo fraud investigator claiming someone had attempted to wire money from his account, which was now “contaminated.” The victim was instructed to wire money to a different account for safekeeping. He sent money to an account opened by Liang at a Capital One Bank branch in Bayside. The next day, most of the money – $90,522 – was wired to a bank in Hong Kong.
•On February 3, 2023, a victim from Port Richey, Florida, wired $48,968.44 to an account Liang had opened at a Capital One branch in Bayside after he was contacted by an individual purporting to be from Amazon saying there were fraudulent purchases on his account. Although the victim did not have an Amazon account, he was told he would be held liable nonetheless for the fraudulent transactions if he did not wire money to “prove his innocence.” Several transfers from the Capital One account were made to a bank in Hong Kong.
•On March 16, 2023, a victim from Hartford, Wisconsin, wired $98,000 to an account Liang had opened at a Chase branch in Bayside after he was contacted by someone claiming to be from the bank’s fraud department. The caller instructed him to wire the money to a “safe account” because his personal information had been compromised. The next day, the money deposited into the Chase account was wired to a China Merchants Bank in China.
•On March 16, 2023, a victim from Rancho Santa Margarita, California, wired $98,000 to an account Liang had opened at a Chase Bank in Bayside after she had been contacted by an individual purporting to be from the Social Security Administration who threatened her with arrest if she did not send money. The next day, money was wired from the Chase account to a China Merchants Bank in China.
•On March 30, 2023, a victim from Delray Beach, Florida, wired $97,010 to an account Liang had opened at a Chase branch in Bayside after he was contacted by someone saying they were from the Social Security Administration and that his bank account and Social Security number had been compromised. The caller told the victim that, in order to safeguard his money, he needed to move the money into a different account.
•Records show that from March 28, 2023, to May 1, 2023, Liang made withdrawals totaling $40,700 from the bogus corporate account he opened with Chase.
On February 25, Liang was arrested in Maryland inside the MGM National Harbor Hotel and Casino, where, records show, he bet more than $2.5 million over a six-month period.
On March 7, Liang was extradited to Queens to face charges.
The investigation was conducted by officers assigned to HSI New York’s El Dorado Task Force Economic Crimes Group, specifically Detective Michael McCaffrey of the NYPD Financial Crimes Task Force/Homeland Security Investigations, and Special Agent Nicholas Yannazzo, of the Social Security Administration, Office of the Inspector General, New York Region.
The investigation was assisted by Jade K. Wilson, trial prep assistant, of the Frauds Bureau of the Queens District Attorney’s Office.
Assistant District Attorney Hana Kim, Deputy Chief of the District Attorney’s Frauds Bureau, is prosecuting the case under the supervision of Assistant District Attorney Joseph T. Conley III, Bureau Chief, and under the overall supervision of Executive Assistant District Attorney for Investigations Gerard Brave.
—
法拉盛华男冒充银行、社安局 电话诈骗六老人63万元
住址报纽约法拉盛45大道的梁飞(Fei Liang,音译)与一名同谋合伙进行电话诈骗,声称他来自社会安全局、银行或供应商,受害者的账户暴露了,要求受害人将钱汇到其它账户进行 “安全保管”,用这种手段骗走了全美多地的六名老人总共近63万美元。
梁男被控六项二级持有赃物罪和一项二级持有赃物未遂罪。如果罪名成立,他最高面临15年监禁。
根据指控,梁男以“JMG Aluminum, Inc.”和“New Century Aluminum, Inc.”的名义,在王后区的三家银行——法拉盛的道明银行(TD Bank)、贝赛(Bayside)的第一资本银行(Capital One)和大通银行(Chase Bank)开设假公司账户,他自称是这两家铝业公司的“总裁”。
2022年10月至2023年3月间,六名受害人向梁的银行账户电汇了共计62万8,278.44美元。
2022年10月5日,康州川布尔镇(Trumbull)的一名受害人的电脑弹出信息,建议他拨打微软公司的一个特定号码,当他致电时,他被告知其电脑发现欺诈活动,他的银行账户可能已泄露,为保护资金安全,提示他将资金汇入另一个账户——梁在法拉盛一家道明银行开设的账户。受害人信以为真,往梁的账户汇入了19万美元。同一天,这笔钱被取走。
2023年1月31日,一名来自迈阿密的受害人,接到“富国银行欺诈调查员”(Wells Fargo fraud investigator)的电话,告知他有人试图从他的账户中汇款,他的账户已经 “被污染”。受害人被指示将钱汇到另一个账户进行保管。他将96,300美元汇到了梁在贝赛Capital One银行的账户。第二天,大部分钱(90,522美元)就被转到了香港的一家银行。
2023年2月3日,一名来自佛州里奇港的受害人接到“亚马逊客服”的电话,说他的账户上有欺诈性购物,虽然受害人没有亚马逊账户,但他被告知,如果他不汇钱 “证明自己清白”,他还是要对欺诈交易负责。他将48,968.44美元汇入梁某在Capital One银行贝赛分行开设的账户,之后,骗子向香港一家银行进行了数次转账,转走了这笔钱。
2023年3月16日,一名来自威斯康星州哈特福德的受害人接到“大通银行诈骗部”人员的电话,说他的个人信息已经泄露,指示他把钱汇到一个 “安全账户”,他遂将9.8万美元汇入了梁在大通银行贝赛分行开设的账户。第二天,这笔钱被汇到了中国的招商银行。
2023年3月16日,一名来自加州Rancho Santa Margarita的受害者被“社会安全局”(Social Security Administration)的人员联系上,威胁她如果不汇款,她就会被捕。她把9.8万美元汇入了梁在贝赛的大通银行开设的账户,第二天,钱就被转到了中国的招商银行。
2023年3月30日,佛州德尔雷海滩(Delray Beach)的受害人接到“社会安全局”人员的电话,称他的银行账户和社会安全号码已被泄露,为了保护他的钱,他需要把钱转到另一个账户。他将97,010美元汇入了梁在贝赛大通分行开设的账户。
记录显示,从2023年3月28日到2023年5月1日,梁从他在大通银行开设的假公司账户中共取款40,700美元。
2月25日,梁在马里兰州的米高梅国家港湾酒店赌场内被捕。记录显示,他在六个月内投注了250多万美元。3月7日,梁被引渡到王后区接受指控。
王后区地区检察官凯兹(Melinda Katz)说,老人经常成为无情骗子的受害者,使他们陷入经济困境,地检办公室将继续积极起诉骗子,并努力教育公众如何防范这些掠夺者。
2024.2.23 币安加密货币交易所、创始人赵长鹏 ( CZ )。美国检察官周五要求法官收紧币安亿万富翁的保释金条款。法庭文件显示,创始人赵长鹏正在等待四月份因违反联邦反洗钱法而被判刑。根据拟议的保释金条款,赵将被要求在国内旅行之前至少提前三天通知检察官和审前服务机构,以便他们有时间提出任何潜在的反对意见。新的保释金条件还将要求赵交出他目前的加拿大护照,并禁止他在未经法院许可的情况下申请新护照。未经事先批准,他还将被禁止改变居住地。文件显示,赵的律师反对这一提议。检察官向西雅图美国地方法院提交的最新文件指出,审前服务官员建议进一步限制赵的行动,只允许他前往华盛顿西区和他目前居住的地区。U.S. prosecutors sought to tighten the bond conditions of billionaire Binance founder Changpeng “CZ” Zhao before he is sentenced for breaking a federal anti-money laundering law. The new bond conditions would order Zhao to surrender his Canadian passport, and provide prosecutors with at least three days’ notice before he travels within the country.
Prosecutors want Binance’s CZ kept on tighter leash ahead of sentencing

U.S. prosecutors Friday asked a judge to tighten the bond conditions of billionaire Binance founder Changpeng “CZ” Zhao as he awaits his April sentencing for breaking a federal anti-money laundering law, court filings show.
Zhao pleaded guilty in late November to a charge of failure to maintain an effective anti-money laundering program in violation of the Bank Secrecy Act, and stepped down as Binance’s CEO at the same time.
Under the proposed bond, Zhao would be required to provide prosecutors and pretrial services with at least three days’ notice before any travel within the country, to give them time to raise any potential objections.
The new bond conditions would also order Zhao to surrender his current Canadian passport, and they would bar him from applying for a new one without the court’s permission. He would also be barred from changing his place of residence without prior approval.
Zhao’s lawyers objected to the proposal, according to the filing. An attorney for Zhao did not immediately respond to CNBC’s request for comment.
Judge Richard Jones barred Zhao from traveling outside the United States in mid-December, after determining that Zhao’s “enormous wealth” and lack of U.S. ties created a risk that he might flee if allowed to return to his home in the United Arab Emirates.
The prosecutors’ latest filing in U.S. District Court in Seattle noted that pretrial services officers have recommended further restricting Zhao’s movement, allowing him to travel only to the western district of Washington and the district where he currently resides.
Pretrial Services also recommended “a location-monitoring condition,” the filing said in a footnote. The filing does not explicitly ask the judge to impose that condition.
2024.2.20 故障iPhone直接換新,一向是Apple給顧客的售後保障。不過,有人利用這一服務,用盜版故障iPhone「狸貓換太子」,到Apple門店更換全新正版iPhone。據美國司法部週二發佈新聞稿顯示,兩名中國籍旅居美國的男性孫浩天(音譯:Haotian Sun,33 歲)和薛鵬飛(音譯:Pengfei Xue,33 歲)在馬利蘭州策劃長時間的詐騙計劃。二人利用盜版iPhone從蘋果公司詐騙超過300萬美金的利潤。據調查,從2017年5月開始,二人便通過空運,收取來自香港的iPhone假貨,然後偽造序號或IMEI號碼,並使用大量化名,提交故障的盜版iPhone給Apple零售店、授權供應商等進行維修,以換取真iPhone。截至2019年9月,他們共向蘋果提交了超過5000部假手機。2019年12月5日,孫浩天和薛鵬飛被逮捕。美國哥倫比亞特區地方法院裁定2人犯下郵件詐騙和共謀欺詐罪,並將面臨最高20年監禁的處罰,案件計劃於 2024 年 6 月 21 日宣判。
PRESS RELEASE
Two Maryland Residents Found Guilty of Multimillion Dollar Scheme to Defraud Apple Inc. out of 5,000 iPhones
For Immediate Release
U.S. Attorney’s Office, District of Columbia
WASHINGTON – Haotian Sun, 33, and Pengfei Xue, 33, both Chinese nationals, were found guilty today by a federal jury for participating in a sophisticated scheme to defraud Apple out of millions of dollars’ worth of iPhones, announced U.S. Attorney Matthew M. Graves; Acting Assistant Attorney General Nicole M. Argentieri, of the Justice Department’s Criminal Division; Inspector in Charge Damon E. Wood, of the United States Postal Inspection Service (USPIS) Washington Division; and Special Agent in Charge Derek W. Gordon, of Homeland Security Investigations, Washington Field Office.
Sun, of Baltimore, and Xue, of Germantown, MD, were found guilty by a federal jury in U.S. District Court in the District of Columbia of conspiracy to commit mail fraud and mail fraud, which carry a statutory maximum sentence of 20 years in prison. U.S. District Court Judge Timothy J. Kelly scheduled sentencing for June 21, 2024.
According to the government’s evidence, between May 2017 and September 2019, Sun, Xue, and other conspirators defrauded Apple Inc. by submitting counterfeit iPhones to Apple for repair to get Apple to exchange them with genuine replacement iPhones. Sun and Xue received shipments of inauthentic iPhones from Hong Kong at UPS mailboxes throughout the D.C. Metropolitan area. They then submitted the fake iPhones, with spoofed serial numbers and/or IMEI numbers, to Apple retail stores and Apple Authorized Service Providers, including the Apple Store in Georgetown. Trial evidence showed that conspirators submitted more than 5,000 inauthentic phones to Apple during the conspiracy, intending to cause a loss of more than $3 million to Apple.
Sun and Xue used various aliases during the scheme. They were arrested on December 5, 2019.
This case was investigated by the U.S. Postal Inspection Service and Homeland Security Investigations.
It is being prosecuted by Assistant U.S. Attorney Kondi J. Kleinman, with the U.S. Attorney’s Office for the District of Columbia, and Trial Attorney Ryan Dickey of the Criminal Division’s Computer Crime and Intellectual Property Section. Essential work was provided by Paralegal Specialists Sona Chaturvedi, Liliana Villamizar, Mariela Andrade, and Amanda Rohde, as well as former Paralegal Specialist Michon Tart, all of the U.S. Attorney’s Office.
2024.2.8 本周二,康州费尔菲尔德(Fairfield)警察局逮捕了一名来自纽约布鲁克林的27岁男子,他涉嫌诈骗一名老人未遂。据警方称,这名男子名叫 Bin Sun ,他假装是技术服务“Geek Squad”的一名成员,并告诉受害者,一大笔钱不小心退到了受害者的账户上,受害者需要归还这笔钱。Sun被控一级盗窃未遂罪。
Fairfield Police Department – Connecticut(康涅狄格州费尔菲尔德警察局官方)
ELDERLY SCAM THWARTED, ARREST MADE:
On February 6, 2024, the Fairfield Police Department arrested Bin Sun (DOB 08/19/1996) of Brooklyn, NY on charges of Criminal Attempt at Larceny 1st Degree (C.G.S. 53a-49/53a-122) following a reported scam targeting an elderly resident.
The investigation began when the victim received an email earlier in the day, purportedly from “Geek Squad,” falsely claiming a $525.00 purchase. To dispute the charge, the victim called the phone number provided in the email and spoke with a male who claimed to be a member of Geek Squad. Believing the interaction to be legitimate, the victim unsuspectingly provided bank account information and granted remote access to her computer, under the false pretense of receiving a refund.
The scammer manipulated the victim into believing a fictitious refund of $25,000.00 had been mistakenly processed. The victim was then coerced into withdrawing $20,000.00 in cash from her bank, with additional plans to collect $5,000.00 the following day. The scammer assured the victim that someone would stop by their home to collect the initial $20,000.
Fairfield Police Detectives, in collaboration with the victim, initiated a surveillance operation to apprehend the scammer. Detectives observed a vehicle park across from the victim’s home, matching the description provided by the scammer. The operator of the vehicle was subsequently identified as Bin Sun (DOB 08/19/1996) and was detained.
Upon detaining Sun, a search revealed a substantial amount of cash on his person. Further investigation revealed that Sun had traveled from Brooklyn, NY, with the intent to fraudulently obtain funds.
Bin Sun (DOB 08/19/1996) was charged with Criminal Attempt at Larceny 1st Degree and was initially held on a $10,000.00 bond. He is scheduled to appear at Bridgeport Superior Court on 02/20/2024. Sun was released from custody after posting the state-required minimum of 7% of his bond.
“This operation highlights the dedication of our Detective Bureau and Patrol personnel in protecting our community from scams targeting vulnerable individuals. Their quick response and decisive action prevented a significant financial loss.”
Residents are urged to remain vigilant against scams, verify communications, and promptly report suspicious activities to police.

A 27-year-old resident of Brooklyn, NY, was arrested by the Fairfield Police Department on Tuesday, in connection with an attempted scam aimed at defrauding an elderly individual.
2024.2.11 一对男女(46岁的Xiaoxia Chen 和她的同伙 44岁的Yongdeng You)被指控在史泰登岛 CVS 药店诈骗 5 万美元礼品卡,Chen 和 You 面临一系列指控,其中包括 1,000 多项伪造和持有伪造仪器的罪名,被告对所有指控均表示不认罪
Woman, man accused in $50K gift-card scam at pharmacies on Staten Island

STATEN ISLAND, N.Y. — Hundreds of gift cards on Staten Island were altered with the purpose of cheating purchasers and their intended recipients out of money, authorities say.
Xiaoxia Chen, 46, a woman, and Yongdeng You, 44, a man, both of Monterey Park, Calif., were arrested on Jan. 31 in connection with the scam, which was perpetrated at multiple CVS locations mostly on the South Shore, according to the criminal complaint.
Authorities recovered 395 gift cards valued at over $50,000 from the defendants at about noon in the vicinity of the 122nd Precinct stationhouse at 2320 Hylan Blvd. in New Dorp, the complaint alleges.
Authorities also allege they confiscated two skimmer devices, three cell phones, a laptop, gloves, tip swabs, glue, hair straighteners, rubbing alcohol, baby wipes and finger protectors from the defendants.
Earlier in January, the defendants placed altered gift cards on the racks “with the intent to defraud the customer” at CVS stores at 2690 Hylan Blvd. in New Dorp, 4055 Hylan Blvd. in Great Kills, 4065 Amboy Road in Great Kills, 2465 Richmond Ave. in New Springville and 1654 Richmond Ave. in Bulls Head, the complaint alleges.
Chen and You left those stores without buying anything, police said.
“I get paid 50 cents per card,” the criminal complaint quotes You as saying to police. “I place them on gift card rack. I get 50 cents for every gift card I take from the gift card rack.”
A law-enforcement source said it is unclear whether the defendants currently live in California or had moved to our area and not yet changed their addresses.
Chen and You face a host of charges that include over 1,000 counts of forgery and possession of a forged instrument in addition to attempted grand larceny, scheme to defraud and unlawful possession of a skimmer device.
The defendants pleaded not guilty to all charges and have been released with non-monetary considerations. They are due back in Criminal Court on March 14, according to public records.
Attorneys for the defendants have not yet responded to requests for comments.
A law-enforcement source said that gift-card scams typically involve stealing a large amount of gift cards and then taking them to a private location where the cards are carefully opened.
In this case, participants in the scheme scratched the cards to reveal the pin numbers, and made a record of the pin and the bar-code numbers, the source said.
They put a sticker over what they scratched off and then they resealed the card so that it looked secure, the source said. After the card was purchased and activated, the perpetrators or other suspects they sold the card information to could use the pins to steal the funds.
The supplies that Chen and You were caught with typically are used by people who perpetrate these scams, the law-enforcement source said.
2024.1.11 The Manhattan District Attorney’s Office is taking action against scammers posing as immigration lawyers and taking advantage of one of New York City’s most vulnerable populations: asylum seekers. D.A. Bragg Announces Indictment of Man for Posing as an Immigration Attorney and Stealing Thousands of Dollars in Fake Legal Fees
曼哈顿地区检察官小阿尔文·布拉格 (Alvin L. Bragg, Jr.)今天宣布起诉 33 岁的巴布洛·伊斯雷尔·奥尔特加·昆卡 (PABLO ISRAEL ORTEGA CUENCA),他因冒充移民律师向众多人收取数千美元的律师费。纽约州最高法院起诉书指控昆卡犯有两项一级移民援助服务罪、两项三级盗窃罪和一项一级诈骗罪。
NEWS • PRESS RELEASES
D.A. Bragg Announces Indictment of Man for Posing as an Immigration Attorney and Stealing Thousands of Dollars in Fake Legal Fees
JANUARY 11, 2024
Manhattan District Attorney Alvin L. Bragg, Jr., today announced the indictment of PABLO ISRAEL ORTEGA CUENCA, 33, for posing as an immigration attorney to numerous people and collecting thousands of dollars in legal fees from them. CUENCA is charged in a New York State Supreme Court indictment with two counts of Immigrant Assistance Services in the First Degree, two counts of Grand Larceny in the Third Degree, and one count of Scheme to Defraud in the First Degree.
“As alleged, New Yorkers looking to become permanent residents trusted Pablo Israel Ortega Cuenca to provide them with legal services, and he broke that trust by taking advantage of them and putting them at risk of deportation,” said District Attorney Bragg. “If you believe you or someone you know has been a victim of this type of fraud, we urge you to call our office’s Immigration Affairs Unit hotline at 212-335-3600 or via WhatsApp at 347-371-0877. Interpreters are available to assist non-native English speakers and we encourage all to reach out regardless of immigration status.”
According to court documents and statements made on the record, from February 2017 until at least October 2019, CUENCA defrauded clients by misleading them about his professional status and the fees required to file certain immigration applications. In at least one instance, he advised an individual to submit a meritless asylum claim, and in others he failed file applications or communicate court dates.
CUENCA misled at least two people into believing that he was an immigration attorney and in doing so also held himself out as either an attorney with the Center for Migration Studies, an employee of the Spanish Consulate, or as a government immigration official. Based on these representations, CUENCA received over $11,000 in legal fees from multiple people.
2024.1.11 Transcript: Office Of Public Safety Holds Briefing On Public Safety In New York City.
So, what are we here to talk about today? We’re here to talk about scams, a lot of scams that take place throughout this particular city. People are cheated out of their property, people are cheated out of their funds. And a lot of these scams have been around for a long time. And let’s think about that for a second. A scam that’s been around for a long time is only around because the scammers continue to find victims for their scams.
Transcript: Office Of Public Safety Holds Briefing On Public Safety In New York City
January 11, 2024
Today, I would like to talk to folks more about the scams that the deputy mayor pointed out are impacting our fellow New Yorkers in the city. There are all sorts of scams where people try and get your money, your personal information from over the phone. You get a robocall, somebody offering free medical devices, free medicine. But there’s a catch. You have to press through the telephone pad to provide your address, your credit card information, all kinds of very key stuff that can’t be released.
The sweepstakes scam. You’ve learned that you won a big prize, but there’s a catch: you have to submit money, send that money in before you can access that prize. The grandparents scam. You get a call in the middle of the night, a loved one needs help. They need money urgently, but only you can help by sending it in, And the law enforcement scam: a call from an officer… Somebody claiming to be an officer, somebody claiming to be from the local precinct that a loved one needs money, needs bail money or that you have a warrant out for your arrest and that you need to pay this warrant over the phone.
These are some of the examples of the scams that we have encountered. And I think the captain also has one [inaudible] here as well, that, let me throw it over to him quickly.
Captain Spiro Papavlasopoulos, Commanding Officer, Crime Prevention Division, Police Department: Absolutely. Hi, deputy mayor. Thank you for having me here today. I work for the Crime Prevention Division, and in the Crime Prevention Division, we are implementing a three‑pronged approach to these scams; the first one is community engagement; the second one is educating the public; and then, the third is effective law enforcement.
So I’m pretty sure everyone at a certain point has probably received either a text message or an e‑mail of someone expressing that you either owe money. But for me to put it a little bit better, I would like to give a quick example of one of the videos that we have of what a typical person might encounter when they receive that phone call.
nyc.gov
https://www.nyc.gov/office-of-the-mayor/news/027-24/transcript-office-public-safety-holds-briefing-public-safety-new-york-city
–
紐約市府11日舉行例行公共安全簡報會,主管公共安全的副市長班克斯(Philip Banks)與市警、市消費者和工人保護局(DCWP),提出目前常見的十種詐騙形式,呼籲民眾慎防。
DCWP對外事務部助理部長歐提斯(Carlos Ortiz)介紹,報稅季將至,目前最常見詐騙的手段是「假IRS騙局」,歹徒在提前錄好的錄音中,假裝是國稅局(IRS),通知被害人補稅,要求在手機輸入個人信息。第二種則是假扮金融機構,提出可以有退稅預支貸款(Tax refund anticipation loan),進而盜取被害人的銀行信息。
「銀行卡盜刷器」(Card Skimmers)與「銀行提款機詐騙」(Bank/ATM Scam)手法雷同,歹徒在商場刷卡器或自動提款機上安裝竊取器,複製受害人卡片信息盜刷。「禮卡詐騙」(Gift Card Scams)則是歹徒提前抄寫商店販售的禮卡信息,在受害人購買並往裡面充錢後,歹徒用已有的號碼盜刷禮卡消費。
另外在亞裔社區常見的「移民詐騙」(Immigration-Related Scams),即不法分子佯裝專業機構,承諾代理受害人的簽證和美國身分申請,進而竊取個人資料、存款信息等。
「珠寶交換詐騙」(Jewelry Swap Scams)則是新型騙局,歹徒假裝急需用錢,變賣身邊珠寶首飾,騙取被害人配戴的真珠寶。「這類歹徒通常瞄準富有同情心、擁有存款財力的長者。」
還有「轉帳捐款詐騙」(Cell Phone Payment/Donation Scam),歹徒偽裝成高中或大學生,向路人要求轉帳支持學生社團,由於索要金額小,受害者通常放鬆警惕,甚至將手機交給歹徒輸入轉帳信息,「有些時候歹徒會趁機多加幾個零,把五元變為5000元,等受害者發現時已為時已晚。」
第九種「複製鑰匙扣」(Key Fob Cloning)則是瞄準粗心民眾,比如把車鑰匙忘在車裡或是家門鑰匙掛在門口,歹徒趁機快速複製鑰匙,擇日將車子偷走或入室盜竊。
最後一種「房屋產權盜竊」(Deed Fraud),歹徒通過竊取房主信息,偽造房屋地契到自己名下。
回复 2 Personal data breaches, confidence and romance scams, non-payment or non-delivery scams, and investment scams, elder fraud, anti-scam, anti-money laundering, charge, sentencing 2024.4- ✓Attorney ✓Gov ✓Police ✓Press ✓U.S.,美国 – 博爪 取消回复